در حال حاضر محصولی در سبد خرید شما وجود ندارد.
This course will teach you the fundamentals needed to configure and manage security in Kubernetes clusters.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


Configuring and Managing Kubernetes Storage and Scheduling

Maintaining, Monitoring and Troubleshooting Kubernetes

LFCE: Linux Service Management – Advanced Email Services

پایه های Kubernetes

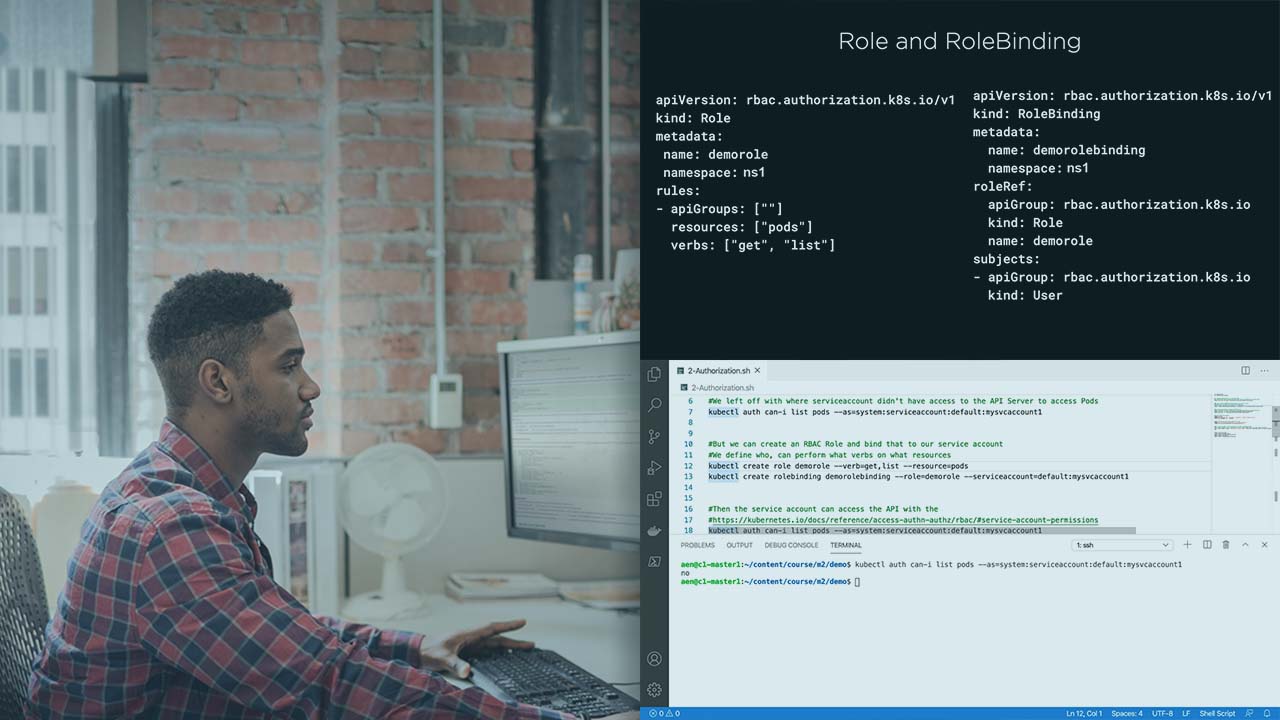
آموزش پیکربندی و مدیریت امنیت در Kubernetes

Managing the Kubernetes API Server and Pods

آموزش کار با سرویس های Azure Kubernetes

LFCE: Linux Service Management – Advanced HTTP Services

Configuring and Managing Kubernetes Networking, Services, and Ingress

Configuring and Managing Kubernetes Networking, Services, and Ingress
اطلاع رسانی حذف دوره های قدیمی و تخفیفات نوروزی مشاهده