در حال حاضر محصولی در سبد خرید شما وجود ندارد.
This intermediate Palo Alto PCNSA training prepares learners to take the PCNSA exam, which is the one required exam to earn the Palo Alto Networks Certified Network Security Administrator (PCNSA) certification.
The Palo Alto Networks Certified Network Security Administrator certification isn’t designed just for security professionals — customers, value-add resellers, pre-sale systems engineers, system integrators, and system administrators can get a lot from it too. The PCNSA focuses on installing, maintaining and managing Palo Alto Networks next-generation firewalls to protect networks — so no matter your role or responsibilities, with our PCNSA training, you’ll understand how to use Palo Alto’s cutting edge tools to protect networks from emerging cyber threats. If you need insight into navigating firewalls on Palo Alto’s security operating system, an extensive background in digital security isn’t a prerequisite for our PCNSA training, and afterwards you’ll be a more capable user of any network secured by Palo Alto.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


فیلم یادگیری F5 BIG-IP Local Traffic Manager

تهدیدهای امنیتی ، حملات و آسیب پذیری ها

آموزش کامل IPv4 DHCP

امنیت سایبری هک کردن کلاه سفید v10

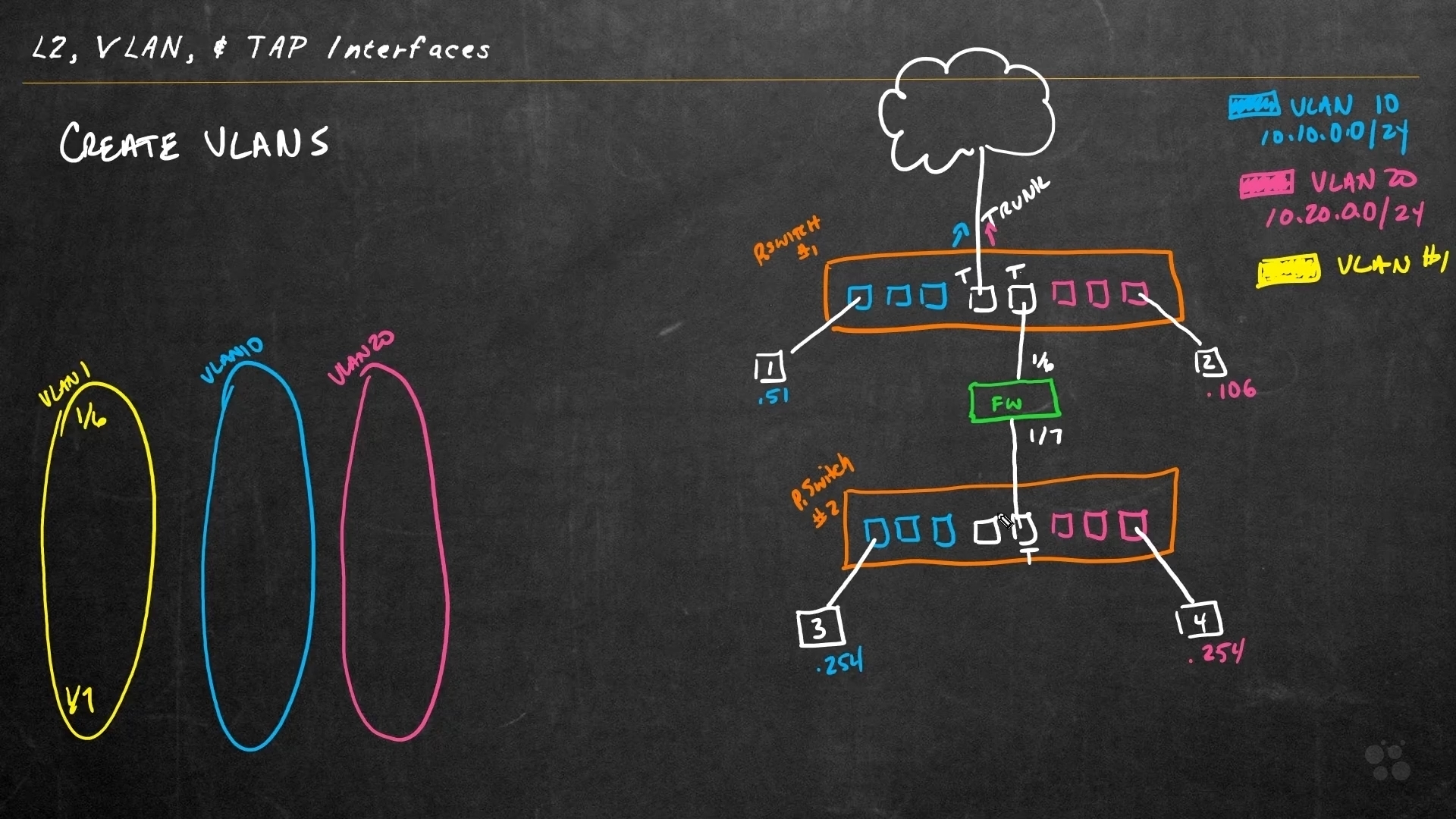
متخصص شدن در امنیت شبکه های Palo Alto

CCT Routing & Switching Online Training
--Optimize-with-Rapid-Spanning-Tree-main-resized.jpg)
آموزش کامل 350-401 ENCOR : بهینه سازی شبکه با Rapid Spanning Tree

احراز هویت در فایروال های FortiGate

فیلم یادگیری Getting Started with Palo Alto Firewalls v8.x
--Configure-and-Verify-First-Hop-Redundancy-Protocols-(FHRP)-main-resized.jpg)
آموزش کامل 350-401 ENCOR : پیکربندی و تست کارکرد پروتکل First Hop Redundancy Protocols (FHRP)