در حال حاضر محصولی در سبد خرید شما وجود ندارد.
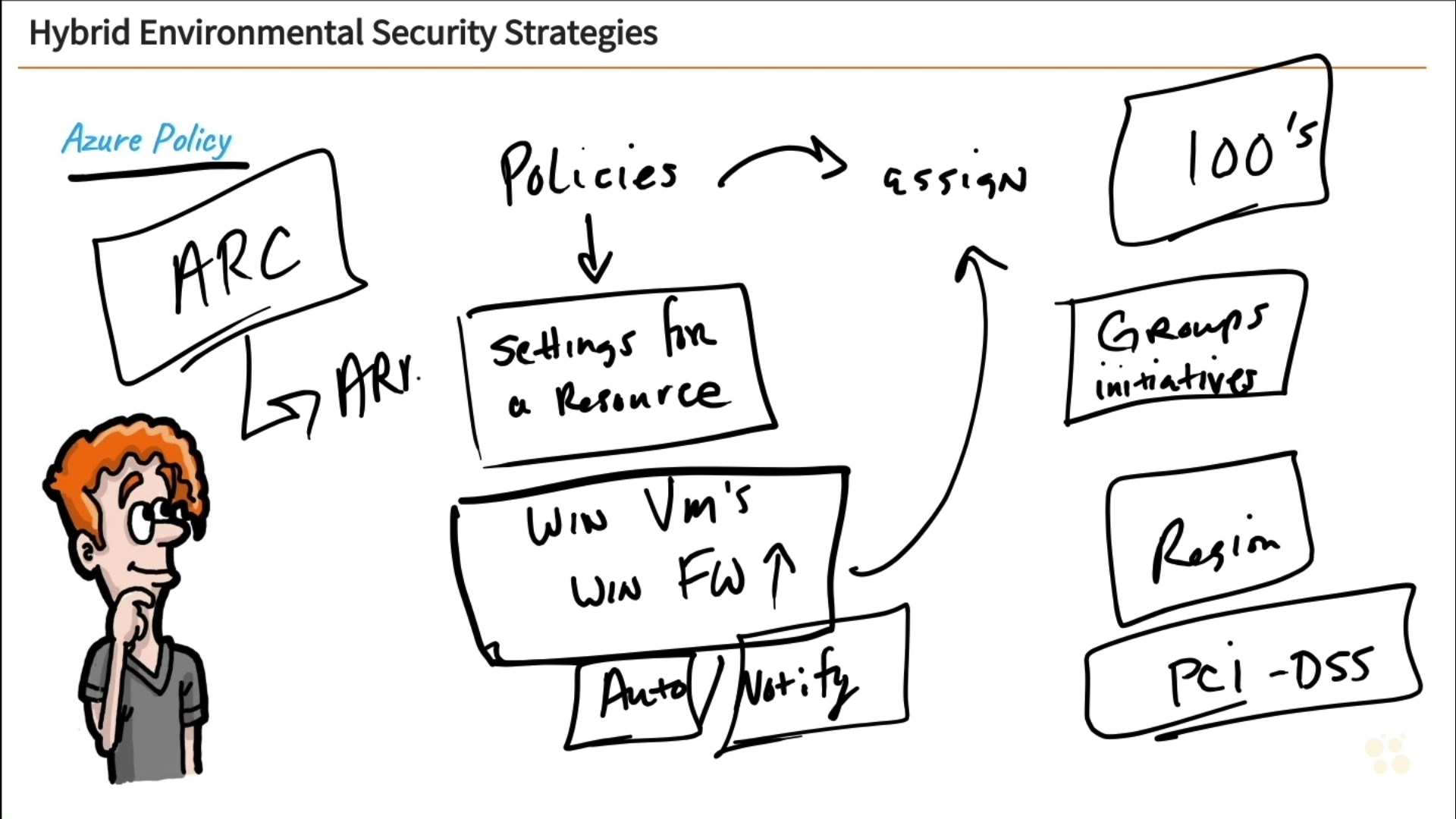
This intermediate SC-100 training prepares learners to design a large network's security architecture that protects its infrastructure, app, and data components, and is grounded in the Zero Trust strategy.
According to Microsoft, an expert cybersecurity architect isn't just a technical master of the individual components, technology, and protocols involved. They're also a master of the soft skills involved with planning a network security posture. In order to earn Microsoft's certification for expert cybersecurity architects, you'll need to show you have the ability to design an enterprise network's security that doesn't just protect a business' network but also advances their business needs in the digital space.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


Azure Security Engineer Associate Online Training

Microsoft Information Protection Administrator (SC-400) Online Training

IT Power Solutions: PDU and UPS Technician Training Online Training

آموزش کار با ابزارهای تست نفوذ

یادگیری امنیت کلود برای توسعه دهندگان نرم افزار

کورس یادگیری رمزنگاری

BIG-IP LTM Specialist: Maintain and Troubleshoot EXAM 301B Online Training

F5 BIG-IP LTM Specialist: Architect, Set up, Deploy (Exam 301a) Online Training

CASP+ Certification Training

Microsoft Information Protection Administrator (SC-400) Online Training
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها