در حال حاضر محصولی در سبد خرید شما وجود ندارد.
This intermediate Microsoft Azure Security Engineer Associate training prepares learners to take the AZ-500 exam, which is the one required exam to earn the Microsoft Certified: Azure Security Engineer Associate certification.
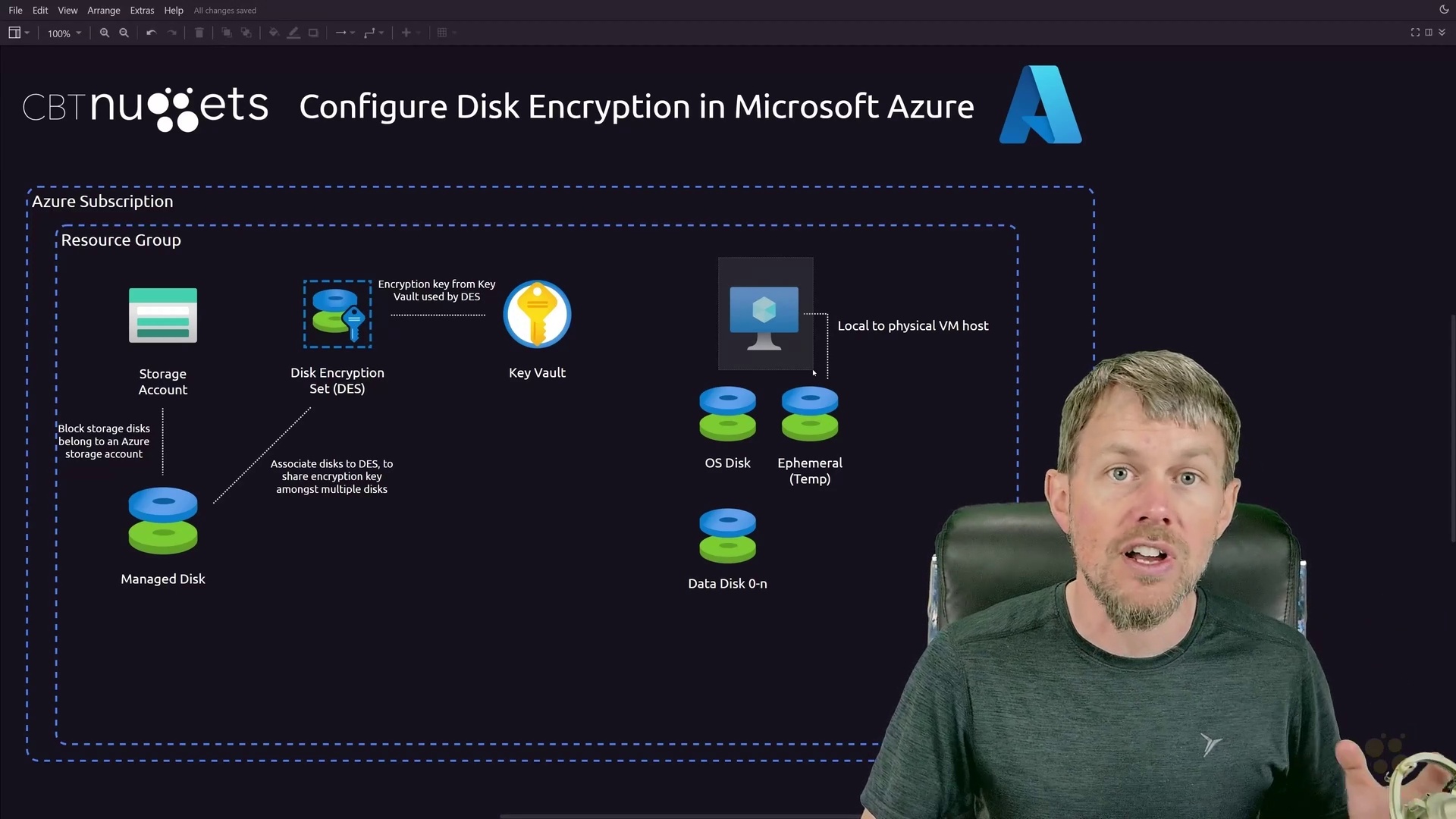
As if staying on top of security threats to standard networks wasn’t enough of a challenge, more and more companies are adopting software-defined network solutions, which come with their own collection of challenges. This training is designed to help IT professionals earn their Microsoft Certified: Azure Security Engineer Associate by covering concepts of Azure-based security, like configuring Azure Active Directory, managing AD privileged identity management, configuring encryption for data at rest and using Azure Key Vault, plus much more.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


Microsoft Information Protection Administrator (SC-400) Online Training
-main-resized.jpg)
دوره یادگیری Certified Cloud Security Professional (CCSP)

Microsoft Information Protection Administrator (SC-400) Online Training

فیلم یادگیری CompTIA PenTest+ Certification

Microsoft Certified: Cybersecurity Architect Expert (SC-100) Online Training

کورس یادگیری رمزنگاری

یادگیری امنیت کلود برای توسعه دهندگان نرم افزار

ISC CISSP آموزش آنلاین گواهینامه 2021
-main-resized.jpg)
تحلیلگر عملیات امنیتی مایکروسافت (SC-200)

(ISC)² CC Online Training