در حال حاضر محصولی در سبد خرید شما وجود ندارد.
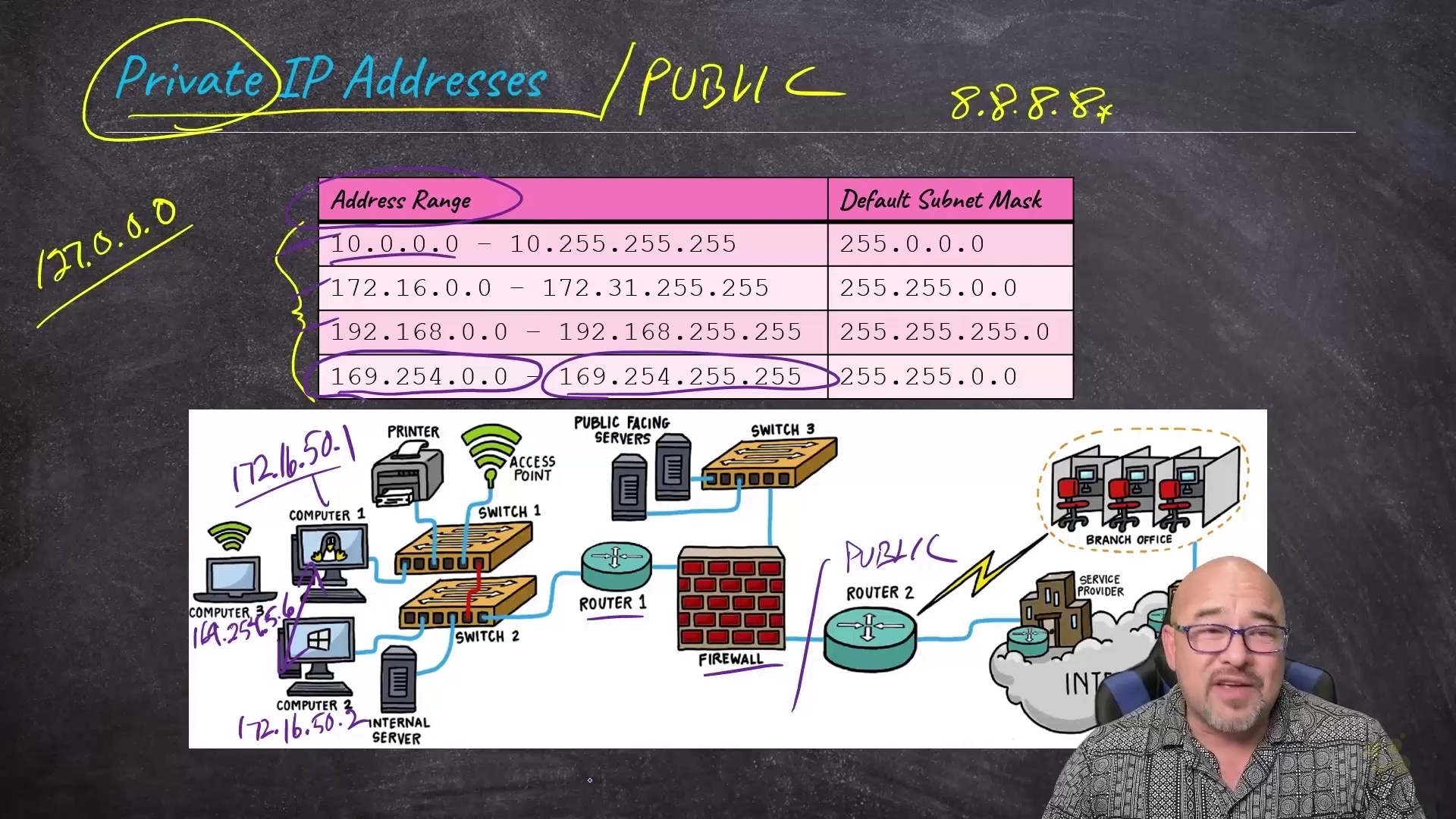
This entry-level CompTIA A+ (220-1102) training prepares learners to work with, manage, and troubleshoot problems with common software and operating systems.
The A+ certification from CompTIA is one of the most well-known entry-level IT certifications in the world. The CompTIA A+ covers computer hardware, Windows and Unix-based operating systems, and networking fundamentals. Like other CompTIA certifications, the CompTIA A+ is vendor-agnostic, which means its lessons apply equally to any operating system or manufacturer.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.

Operating System Fundamentals Online Training

IT Fundamentals (ITF+) Online Training

کورس یادگیری مفاهیم دیتابیس ها

کورس مبانی سیستم عامل ها

Microsoft 365 Certified: Modern Desktop Administrator Associate (MD-100) Online Training

Windows Server Hybrid Administrator Associate Certification Training

ساخت کانتینرهای Windows Server 2022 بوسیله Docker

SC-900 Training: Microsoft Certified: Security, Compliance, and Identity Fundamentals

LPI Linux Essentials Online Training

Linux Professional Institute Security Essentials (020-100) Online Training
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها