در حال حاضر محصولی در سبد خرید شما وجود ندارد.
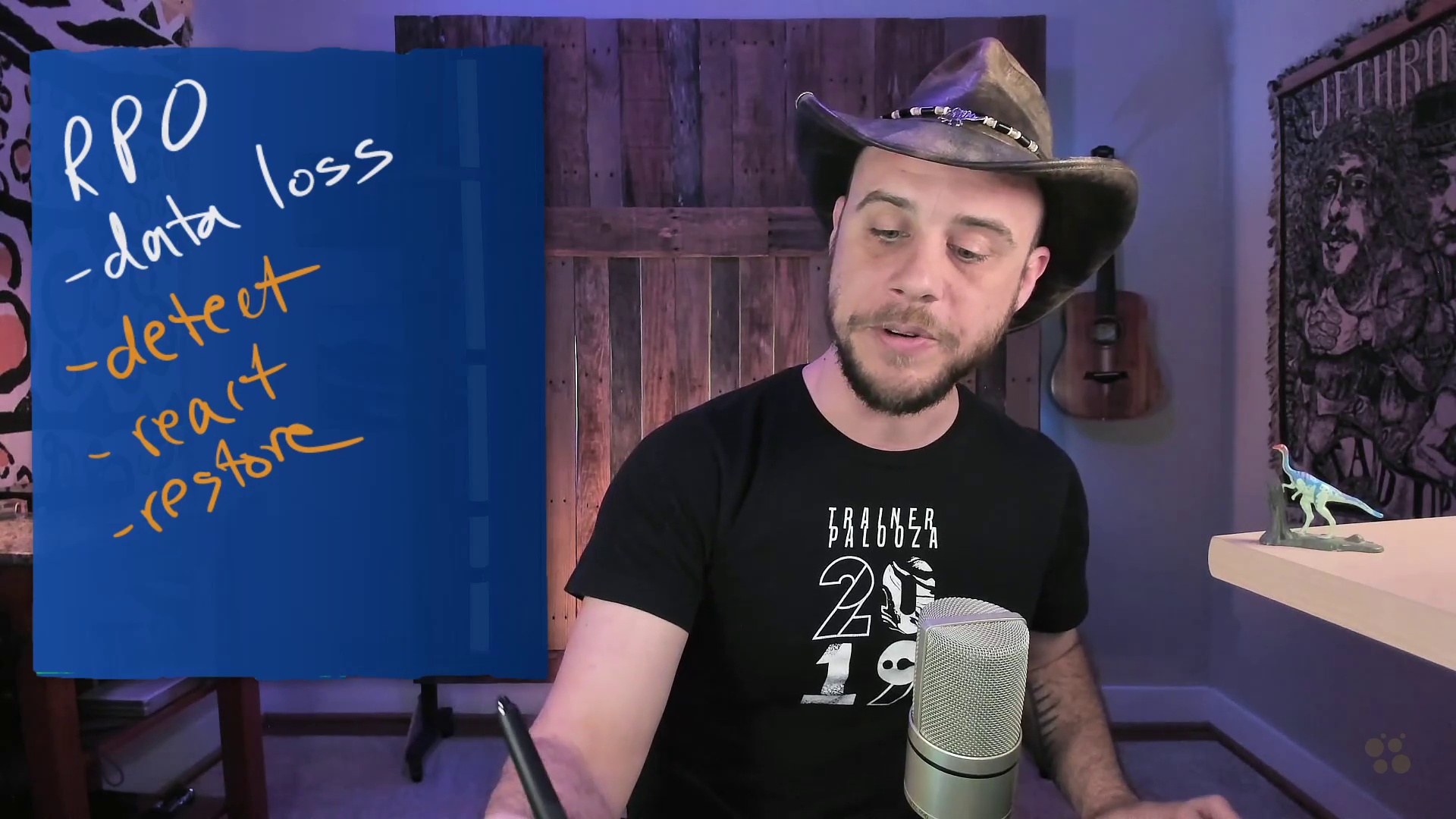
This foundational CompTIA Cloud+ training prepares cloud specialists to take the CV0-003 exam, which is the one required exam to earn the Cloud+ certification.
With vendor-neutral training you may not know a certain cloud provider's deepest, darkest UI shortcuts, but you have a wide understanding of what's possible in the cloud and how to accomplish it. No matter what service or manufacturer you find yourself on.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


AWS Certified Solutions Architect Online Training

فیلم یادگیری Deploy Juniper vSRX Firewall on AWS

AWS Certified Developer Associate Training

Fundamental Cloud Computing Concepts Online Training

AWS Certified Developer Associate Training

Fundamental Cloud Security Online Training

متخصص کلود AWS شوید
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها