1. Protocol Basics, Traffic Sniffing, and Recon - Part 1
2. Protocol Basics, Traffic Sniffing, and Recon - Part 2
3. Protocol Basics, Traffic Sniffing, and Recon - Part 3
4. Protocol Basics, Traffic Sniffing, and Recon - Part 4
5. Security Standards for Personal Networks - Part 1
6. Security Standards for Personal Networks - Part 2
7. Security Standards for Personal Networks - Part 3
8. Security Standards for Personal Networks - Part 4
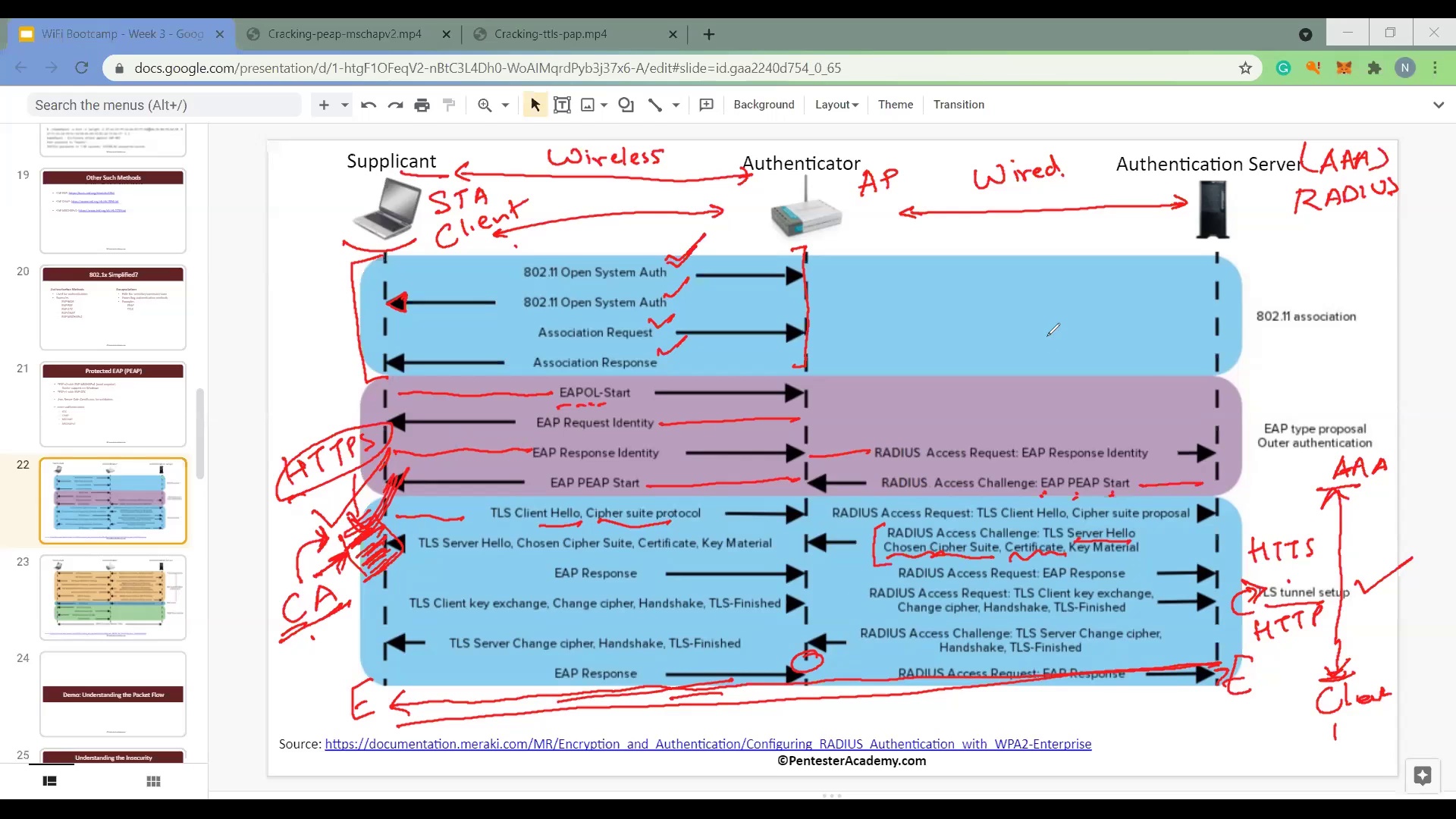
9. Security Standards for Enterprise Networks - Part 1
10. Security Standards for Enterprise Networks - Part 2
11. Security Standards for Enterprise Networks - Part 3
12. Security Standards for Enterprise Networks - Part 4
13. Advanced Pivoting, Relay Attacks, Understanding WPA3 - Part 1
14. Advanced Pivoting, Relay Attacks, Understanding WPA3 - Part 2
15. Advanced Pivoting, Relay Attacks, Understanding WPA3 - Part 3
16. Advanced Pivoting, Relay Attacks, Understanding WPA3 - Part 4