در حال حاضر محصولی در سبد خرید شما وجود ندارد.
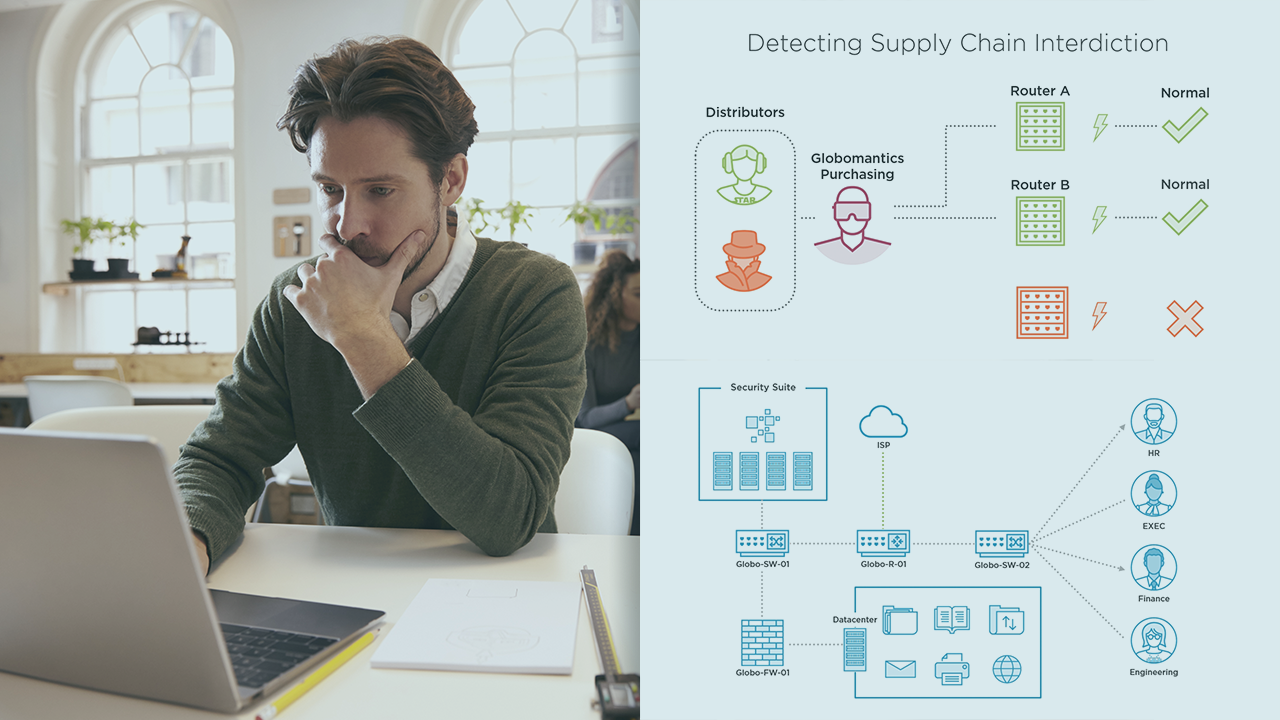
In this course on system anomaly detection, you will explore the use of CPU, RAM, GPU, fans, and power resource usage data to reveal various advanced attacker techniques and uncover events associated with hardware supply chain interdiction.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


Blue Team Tools: Defense against Adversary Activity Using MITRE Techniques

OS Analysis with HELK

Security Event Triage: Revealing Attacker Methodology in Web Application Events

Trickbot Banking Trojan

Security Event Triage: Detecting Network Anomalies with Behavioral Analysis

Blue Team Tools: Defense against Adversary Activity Using MITRE Techniques

Security Event Triage: Operationalizing Security Analysis

آموزش انجام آنالیزهای امنیت در شبکه

Linux Endpoint Security: Processes

Setting Up a Malware Analysis Lab
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها