در حال حاضر محصولی در سبد خرید شما وجود ندارد.
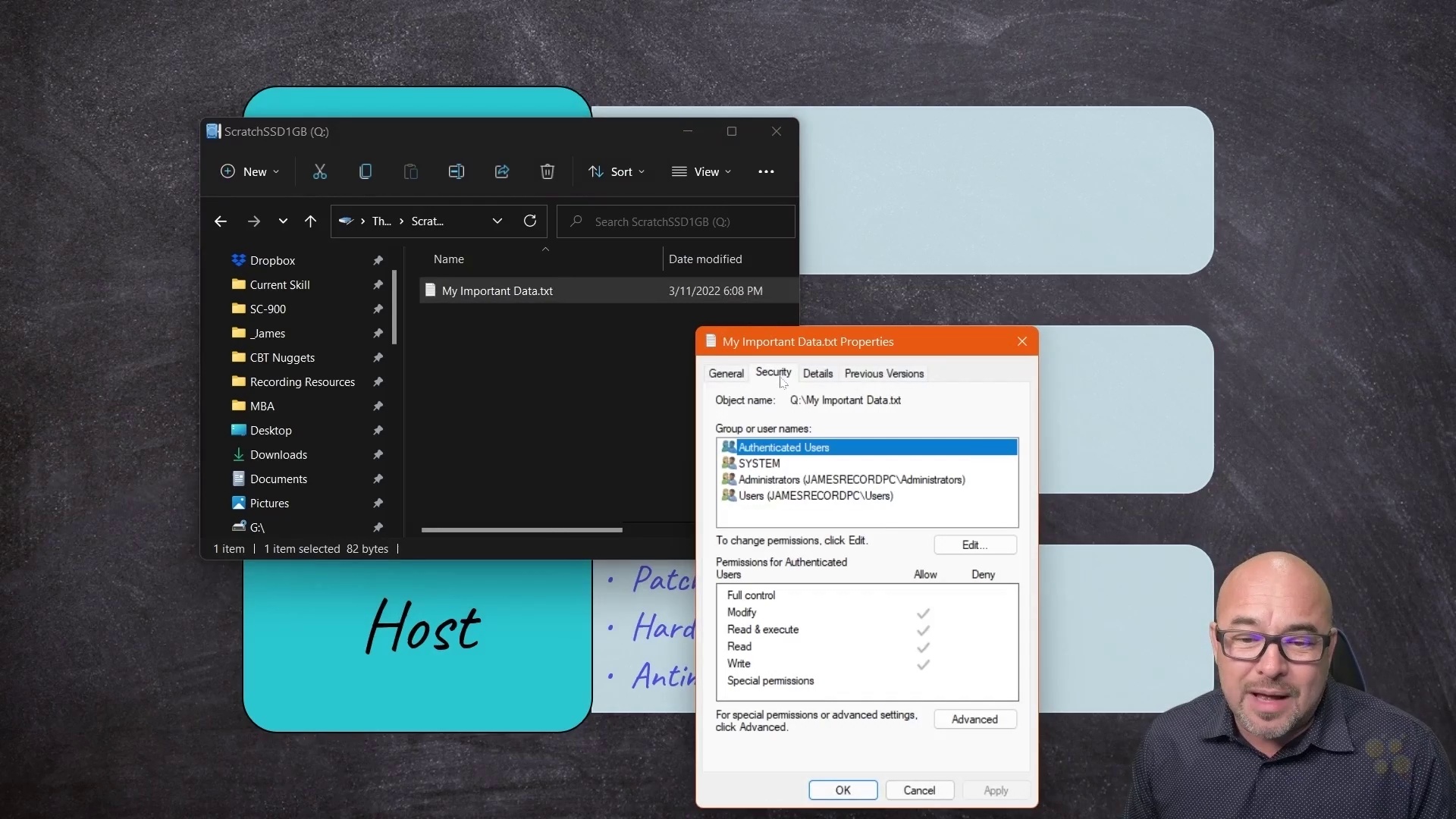
This foundational Microsoft Certified: Security, Compliance, and Identity Fundamentals training covers the objectives in the SC-900 exam, which is the one required exam to earn the Microsoft Certified: Security, Compliance, and Identity Fundamentals certification.
It's hard to overstate how important security, compliance and identity are to network stability and reliability. Those three concepts are so important that everyone who touches a network's operations – from administrators to managers to executive stakeholders – should consider training in the basic concepts around security, compliance and identity (SCI). This Microsoft Certified: Security, Compliance, and Identity Fundamentals training prepares learners for passing the SC-900 and earning an entry-level certification, but the knowledge within it is highly valuable for anyone who makes decisions that affect networks and their security.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


LPI Linux Essentials Online Training

LPI Linux Essentials Online Training

Microsoft 365 Certified: Endpoint Administrator Associate (MD-102) Online Training

ITCA – Cybersecurity Fundamentals Online Training

ساخت کانتینرهای Windows Server 2022 بوسیله Docker

مدیریت هویت و دسترسی با ابزارهای Microsoft

آموزش آنلاین Hyper-V

Operating System Fundamentals Online Training

یادگیری Active Directory : کار با Domain Services
-main-resized.jpg)
آموزش صدور گواهینامه Windows Server Hybrid Administrator
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها