در حال حاضر محصولی در سبد خرید شما وجود ندارد.
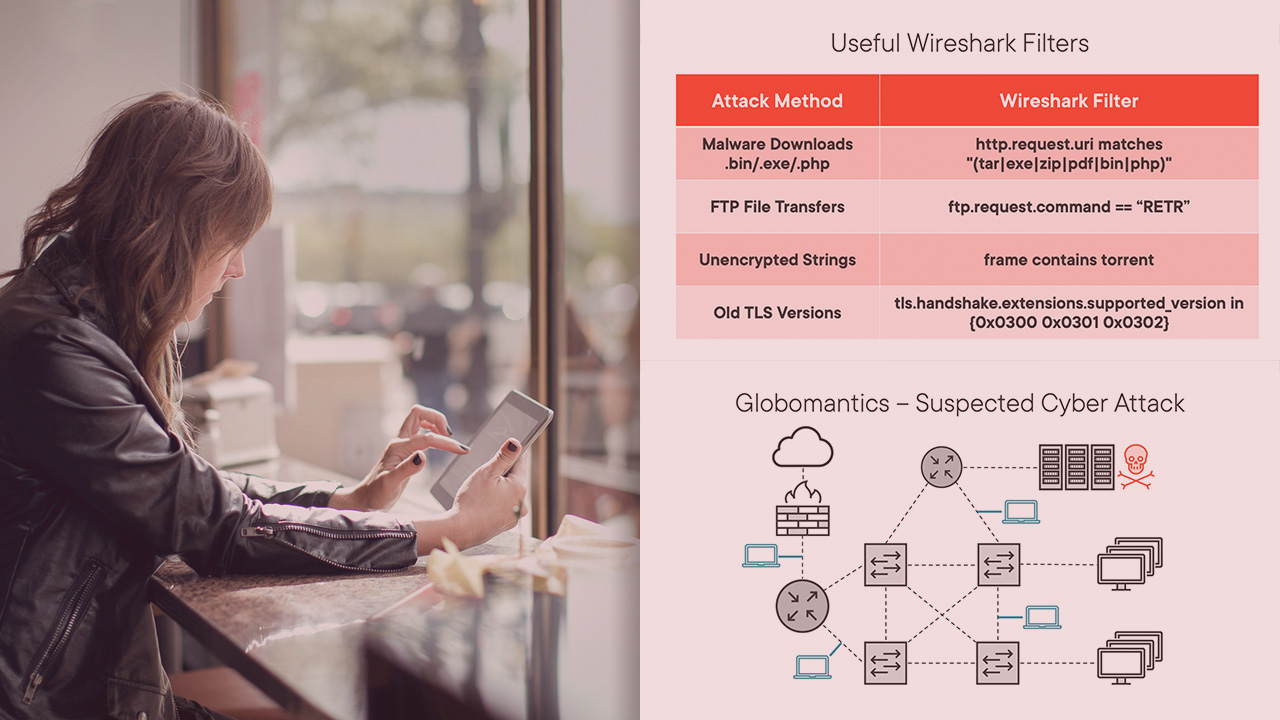
This course will teach you how to quickly spot cyber attacks and indicators of compromise in network traffic with Wireshark.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


Mastering TCP Analysis with Wireshark

Analyzing Network Protocols with Wireshark

Getting Started with Nmap – The Ultimate Hands-On Course

Protocol Deep Dive: QUIC

Foundational TCP Analysis with Wireshark

Troubleshooting Slow Networks with Wireshark

Protocol Deep Dive: QUIC

Protocol Deep Dive: QUIC

Wireshark Configuration for Cyber Security Analysis

Visualizing Network Traffic with Wireshark
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها