01. Module Overview
02. Risk Types
03. Managing Risk
04. Risk Management Defined
05. Risk Management Concepts
06. Strategic Options
07. Risk Register, Risk Matrix, and Heat Map
08. Risk Control Self-assessment (RCSA)
09. Risk Awareness (Inherent, Residual, Control, and Risk Appetite)
10. Regulatory Examples
11. Gramm-Leach-Bliley Act (GLBA)
12. HIPAA
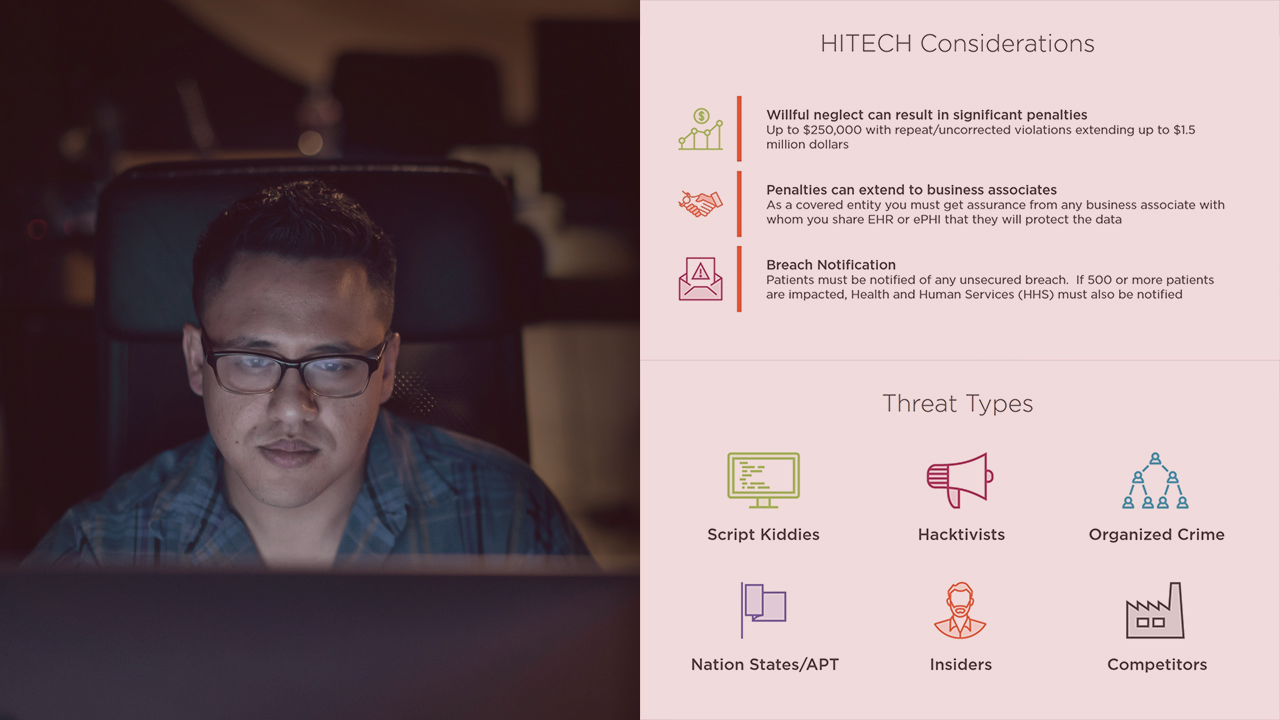
13. HITECH Act
14. Sarbanes-Oxley Act (SOX)
15. GDPR
16. Qualitative and Quantitative Analysis
17. Risk Calculation
18. Likelihood of Threat
19. Impact of Threat
20. Loss Calculation Terms (ALE, SLE, and ARO)
21. Threat Assessment (Disaster)
22. Additional Risk Calculation Terms (MTBF, MTTF, and MTTR)
23. Business Impact Analysis- Key Terminology
24. Mission Essential Functions
25. Identification of Critical Systems
26. Single Point of Failure (SPOF)
27. Order of Restoration
28. Phased Approach
29. Identifying Most Critical Systems First
30. Risk Assessment
31. Continuity of Operations
32. IT Contingency Planning