در حال حاضر محصولی در سبد خرید شما وجود ندارد.
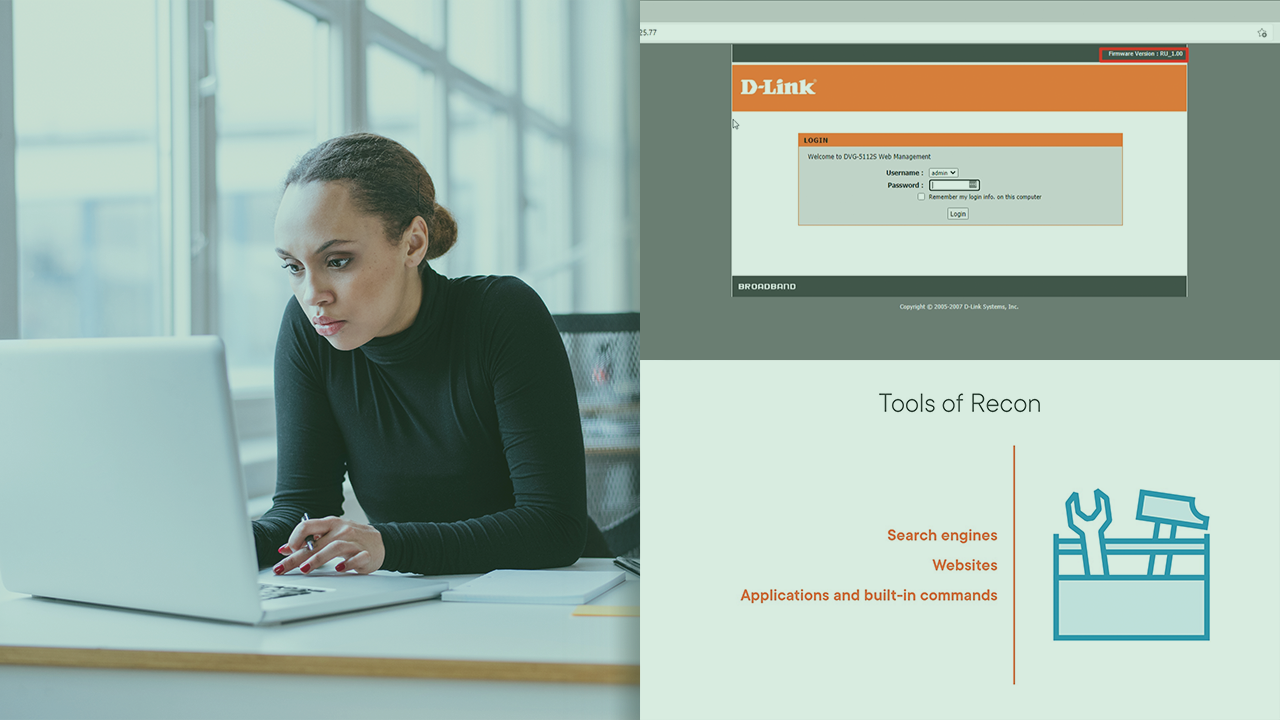
Reconnaissance/Footprinting is the first phase attackers perform. This course will teach you the skills attackers use, which is needed for the CEH Exam.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


کورس یادگیری کامل Ethical Hacking: Understanding Ethical Hacking
آموزش تست برنامه های کاربردی در مسیر CompTIA PenTest+

فیلم یادگیری کامل Compliance and Assessment for CompTIA CySA+

Ethical Hacking: Vulnerability Analysis

کورس یادگیری کامل Ethical Hacking: Hacking Wireless Networks

Ethical Hacking: Malware Threats
-main-resized.jpg)
فیلم یادگیری Ethical Hacking: Hacking the Internet of Things (IoT)

کورس یادگیری Ethical Hacking: Scanning Networks

کورس یادگیری کامل Ethical Hacking: Understanding Ethical Hacking

Password and Wireless Attacks with Kali Linux