1.CCSA Exam Objectives and CheckMates
2.Check Point Security Product Lineup
3.Security Gateway Software Blades
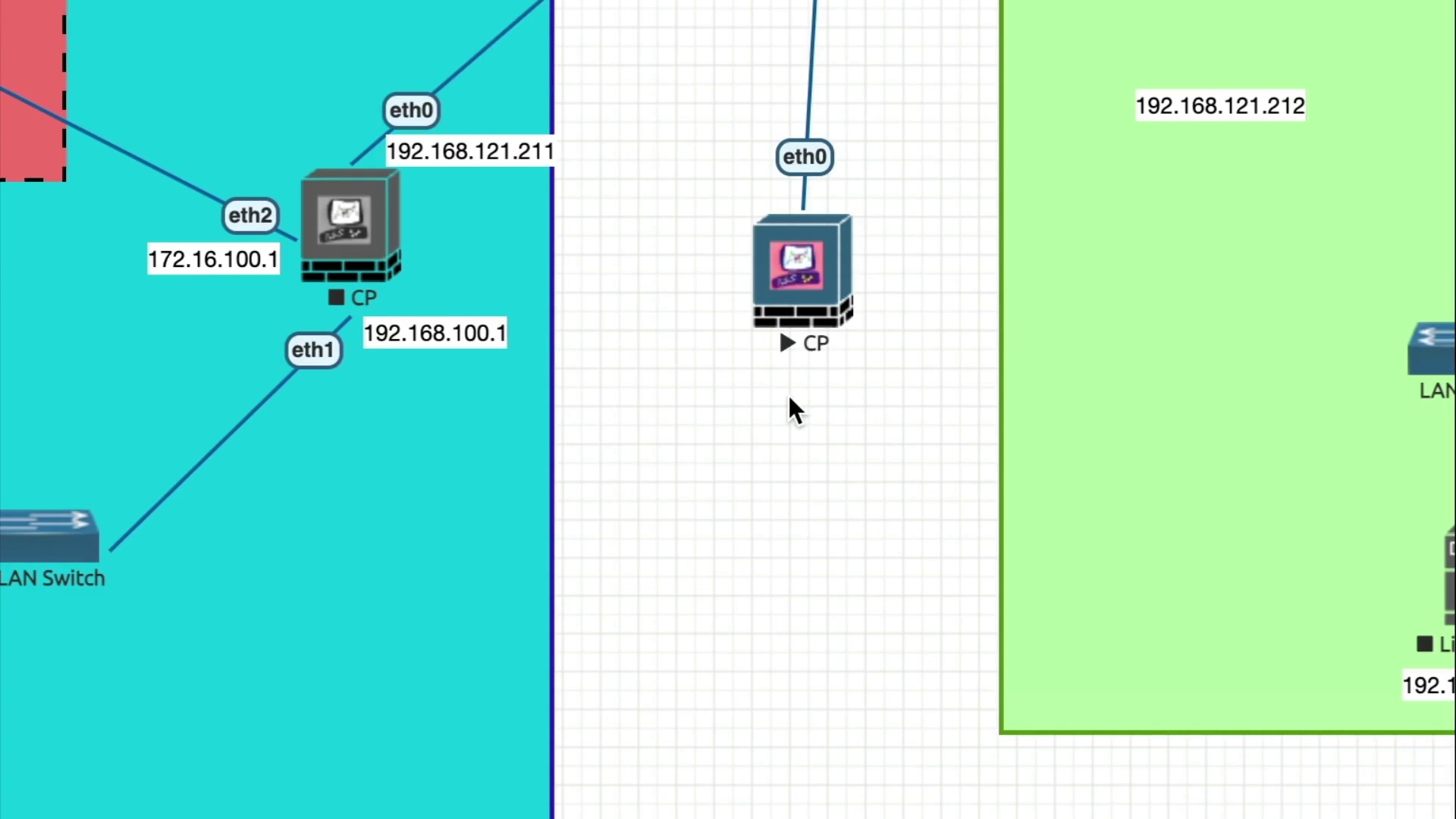
4.Check Point Deployment Methods
5.Physical Check Point Security Gateway Features
6.Check Point Licensing
7.Validation
8.Hands-On Lab or Other Video
9.Hands-On Lab or Other Video
Question 1-question.txt
Question 2-question.txt
Question 3-question.txt
Question 4-question.txt
Question 5-question.txt
Question 6-question.txt
Question 7-question.txt
Question 8-question.txt
Question 9-question.txt
Question 10-question.txt
Question 11-question.txt
Question 12-question.txt
saved url-.txt
saved url-Check Point Security Gateway Models.txt
saved url-Check Point Security Product Lineup.txt