در حال حاضر محصولی در سبد خرید شما وجود ندارد.
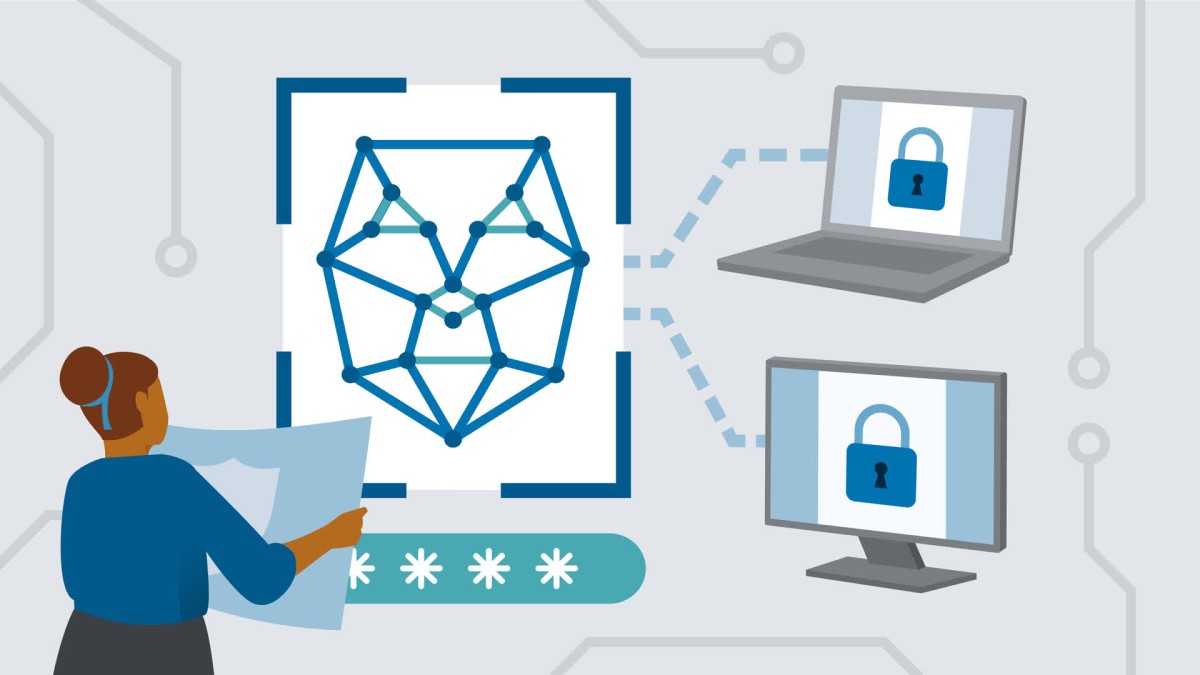
The course provides network professionals with a comprehensive exploration of identity and access management. Instructor Liam Cleary covers the fundamentals of IAM, including authentication mechanisms, authorization, access control techniques, and the intricacies of account management and identity federation. Liam also focuses on implementing IAM in cloud environments and strategies for monitoring and reporting to ensure robust security.
Advanced topics such as security protocols, encryption, and privileged access management (PAM) are also covered, along with practical aspects of integrating IAM with network infrastructure and automating IAM tasks using tools like PowerShell and Python.
Whether you want to deepen your existing knowledge or branch out into new areas of network security, this course combines theory with practical application, preparing you to manage identities and secure access effectively in any network environment.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


آموزش کدنویسی و استفاده از PowerShell Background Jobs

فیلم یادگیری Microsoft 365: Manage Governance and Compliance

Getting Started with PowerShell Scripting

Monitoring, Troubleshooting, and Optimizing SharePoint 2016

Continuous Monitoring with PowerShell

آموزش مبانی و مفاهیم SharePoint Server

دوره یادگیری Configuring SharePoint 2016 Workloads

Managing Computers with PowerShell and CIM

Using the Microsoft Graph PowerShell SDK

آموزش پیاده سازی Authentication در شیرپوینت 2019
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها