Course Introduction
Domain Introduction Application Deployment Domain Objecties
Domain Introduction Application Design and Build Domain Objecties
Domain Introduction Application Enironment, Configuration & Security Domain Objecties
Domain Introduction Application Obserability & Maintenance Domain Objecties
Domain Introduction Serices & Networking Domain Objecties
Lesson 1.1 Oeriew and Objecties
Lesson 1.2 Domains and Curriculum Details
Lesson 1.2 Domains and Curriculum Details (1)
Lesson 1.3 Exam Enironment and Tips
Lesson 1.4 Exam Preparation and Practice Tests
Lesson 2.1 Introduction to Kubernetes
Lesson 2.2 High-leel Kubernetes Architecture
Lesson 2.3 Adantages of using Kubernetes
Lesson 3.1 Kubernetes Primities and Objects
Lesson 3.2 Managing Objects with kubectl
Lesson 3.3 Object Management Exam Essentials
Lesson 4.1 Introduction to Container Fundamentals
Lesson 4.2 Building Container Images and Running Containers
Lesson 4.3 Exercise Defining, Building, and Running a Container Image
Lesson 4.4 Container Fundamentals Exam Essentials
Lesson 5.1 Introduction to Pods and Namespaces
Lesson 5.2 Running and Configuring Applications in Containers with Pods
Lesson 5.3 Grouping Objects in Namespaces
Lesson 5.4 Exercise Creating, Inspecting, and Interacting with a Pod in a Namespace
Lesson 5.5 Pods and Namespaces Exam Essentials
Lesson 6.1 Introduction to Jobs and CronJobs
Lesson 6.2 Jobs Executing one-time operations with Jobs
Lesson 6.3 Exercise Creating and inspecting a Job
Lesson 6.4 CronJobs Executing Periodic Operations with CronJobs
Lesson 6.5 Exercise Creating and inspecting a CronJob
Lesson 6.6 Jobs and CronJobs Exam Essentials
Lesson 7.1 Introduction to Volumes
Lesson 7.2 Using Ephemeral Volumes in Pods
Lesson 7.3 Exercise Creating and Using an Ephemeral Volume
Lesson 7.4 Proisioning Persistent Volumes and Using them in a Pod
Lesson 7.5 Exercise Creating and using a Persistent Volume using static Proisioning
Lesson 7.6 Volumes Exam Essentials
Lesson 8.1 Introduction to Multi-Container Pods
Lesson 8.2 Understanding Init containers
Lesson 8.3 Exercise Adding an init Container
Lesson 8.4 Understanding Common Multi-Container Design Patterns
Lesson 8.5 Exercise Implementing the Adapter Pattern
Lesson 8.6 Exercise Implementing the Ambassador Pattern
Lesson 8.7 Multi-Container Pods Exam Essentials
Lesson 9.1 Introduction to Labels and Annotations
Lesson 9.2 Understanding Labels
Lesson 9.3 Understanding Annotations
Lesson 9.4 Exercise Using Labels and Annotations
Lesson 9.5 Labels and Annotations Exam Essentials
Lesson 10.1 Introduction to Deployments
Lesson 10.2 Exercise Performing Rolling Updates and Manually Scaling a Deployment
Lesson 10.3 Autoscaling Workloads
Lesson 10.4 Exercise Creating a Horizontal Pod Autoscaler for a Deployment
Lesson 10.5 Deployment Strategies
Lesson 10.6 Exercise Implementing the Blue-Green Deployment Strategy
Lesson 10.7 Deployment Exam Essentials
Lesson 11.1 Introduction to Helm
Lesson 11.2 Discoering and Installing a Public Helm Chart
Lesson 11.3 Exercise Installing an Existing Helm Chart from the Central Chart Repository
Lesson 11.4 Building and Installing a Custom Helm Chart
Lesson 11.5 Exercise Implementing, Packaging, and Installing a Custom Helm Chart
Lesson 11.6 Helm Exam Essentials
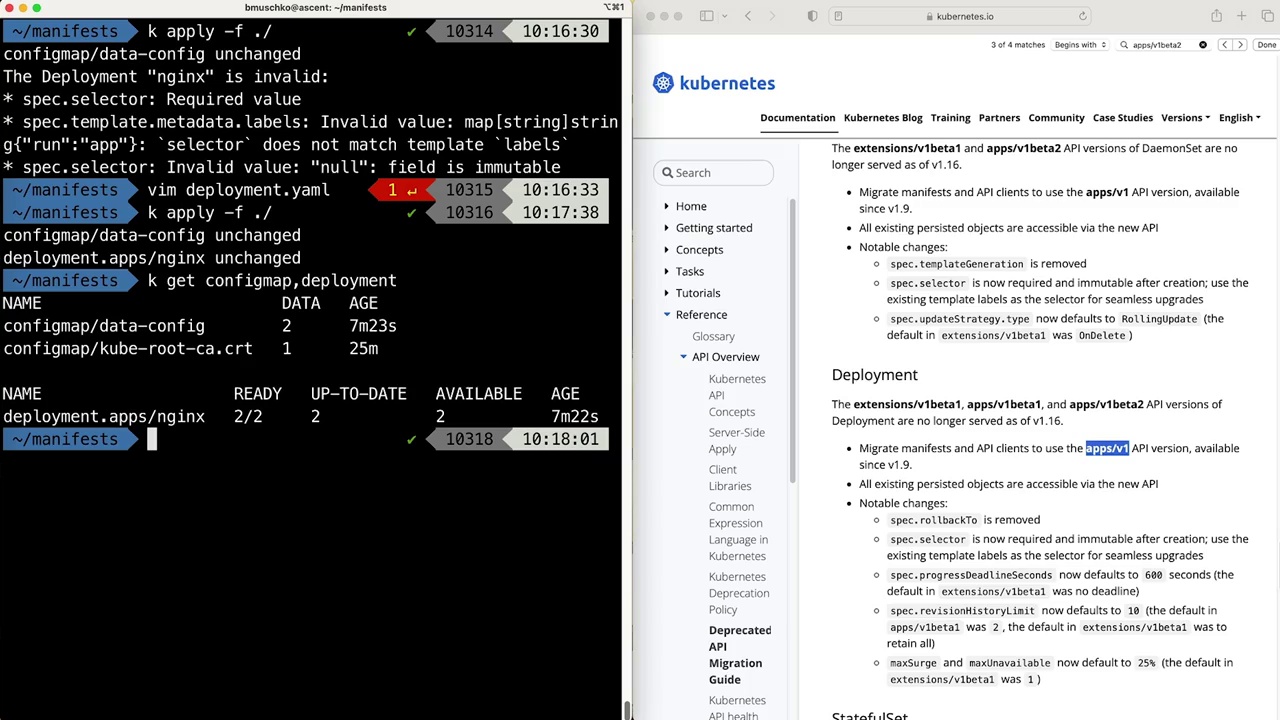
Lesson 12.1 Introduction to API Deprecations
Lesson 12.2 API Deprecation Scenarios by Example
Lesson 12.3 Exercise Identifying and Replacing a Deprecated API
Lesson 12.4 API Deprecations Exam Essentials
Lesson 13.1 Introduction to Probes
Lesson 13.2 Health Probes and Verification Methods
Lesson 13.3 Exercise Defining Probes for a Container
Lesson 13.4 Probes Exam Essentials
Lesson 14.1 Introduction to Metrics Serer
Lesson 14.2 Collecting and Rendering Node and Pod Resource Metrics
Lesson 14.3 Exercise Determining Metrics for Pods
Lesson 14.4 Metrics Serer Exam Essentials
Lesson 15.1 Introduction to Troubleshooting Pods and Containers
Lesson 15.2 Troubleshooting Techniques
Lesson 15.3 Exercise Troubleshooting a Pod that has Issues at Runtime
Lesson 15.4 Troubleshooting Pods and Containers Exam Essentials
Lesson 16.1 Introduction to Custom Resource Definitions (CRDs)
Lesson 16.2 Understanding a CRD by Example
Lesson 16.3 Exercise Defining and Interacting with a CRD
Lesson 16.4 Custom Resource Definitions (CRDs) Exam Essentials
Lesson 17.1 Introduction to Authentication and Authorization
Lesson 17.2 Authentication ia credentials in kubeconfig
Lesson 17.3 Role-based Access Control (RBAC)
Lesson 17.4 Using a SericeAccount with RBAC
Lesson 17.5 Exercise Regulating Access to API Resources with RBAC
Lesson 17.6 Authentication and Authorization Exam Essentials
Lesson 18.1 Introduction to Resource Management
Lesson 18.2 Defining Container Resource Requests and Limits
Lesson 18.3 Exercise Defining Container Resource Requests and Limits
Lesson 18.4 Constraining Resource Consumption with a ResourceQuota
Lesson 18.5 Exercise Defining a Resource Quota for a Namespace
Lesson 18.6 Constraining or Defaulting Resource Allocations with a LimitRange
Lesson 18.7 Exercise Creating a Pod Conforming with LimitRange in Namespace
Lesson 18.8 Resource Management Exam Essentials
Lesson 19.1 Introduction to ConfigMaps and Secrets
Lesson 19.2 Creating and consuming a ConfigMap
Lesson 19.3 Exercise Representing a file in a ConfigMap and Mounting it as a Volume
Lesson 19.4 Creating and Consuming a Secret
Lesson 19.5 Exercise Representing Plain-Text Values in a Secret and Injecting them as Enironment Variables
Lesson 19.6 ConfigMaps and Secrets Exam Essentials
Lesson 20.1 Introduction to Security Context
Lesson 20.2 Defining Container Security Settings by Example
Lesson 20.3 Exercise Defining a Security Context on the Pod- and Container-leel
Lesson 20.4 Security Context Exam Essentials
Lesson 21.1 Introduction to Serices
Lesson 21.2 Exposing a Stable Network Endpoint to Pods with a Serice
Lesson 21.3 Exercise Routing Traffic to Pods from Inside and Outside of a Cluster
Lesson 21.4 Serices Exam Essentials
Lesson 22.1 Introduction to Troubleshooting Serices
Lesson 22.2 Troubleshooting Techniques for Serices
Lesson 22.3 Exercise Troubleshooting a Serice
Lesson 22.4 Troubleshooting Serices Exam Essentials
Lesson 23.1 Introduction to Ingresses
Lesson 23.2 Route HTTP(S) Traffic from the Outside of the Cluster to Serice(s)
Lesson 23.3 Exercise Defining and using an Ingress without TLS
Lesson 23.4 Ingresses Exam Essentials
Lesson 24.1 Introduction to Network Policies
Lesson 24.2 Constraining Network Communication between Pods
Lesson 24.3 Exercise Restricting access to and from a Pod with Network Policies
Lesson 24.4 Network Policies Exam Essentials