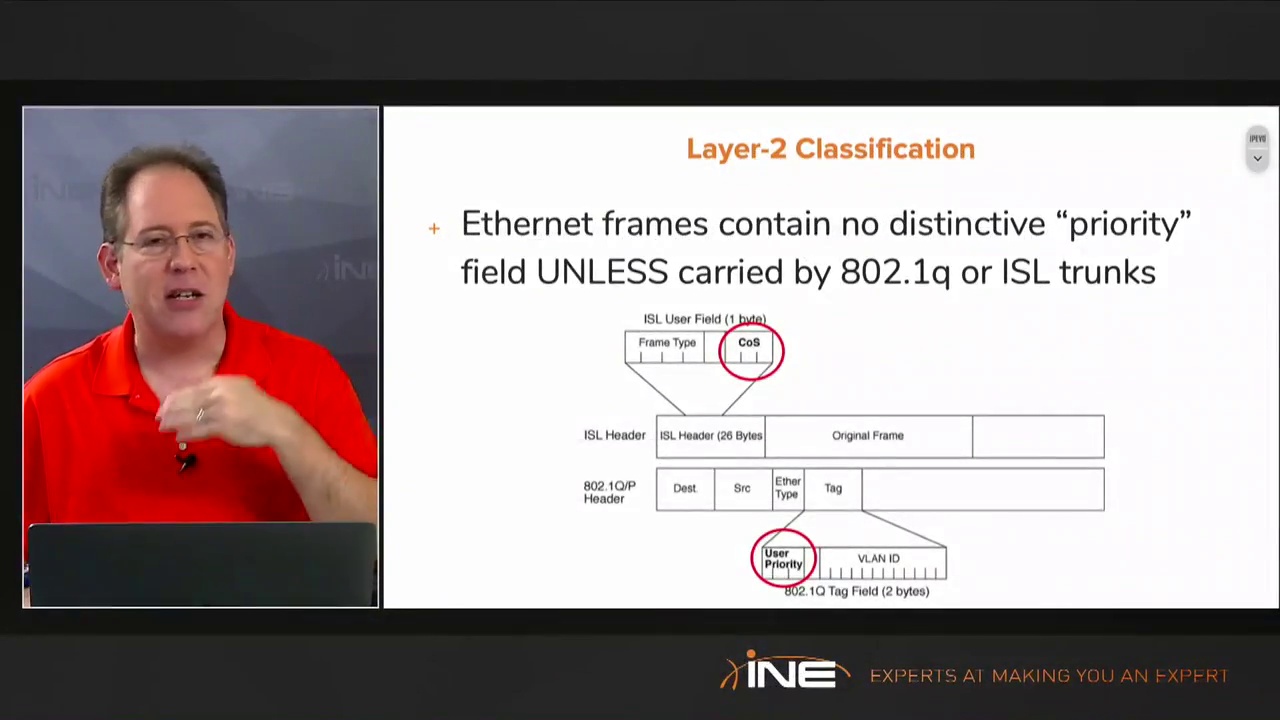
INE-wireshark-technologies-course-slides INE-Wireshark-Technologies-1.1.1.pdf
INE-Wireshark-Technologies-1.1.2.pdf
INE-Wireshark-Technologies-1.1.3.pdf
INE-Wireshark-Technologies-1.1.4.pdf
INE-Wireshark-Technologies-1.2.1.pdf
INE-Wireshark-Technologies-1.2.2.pdf
INE-Wireshark-Technologies-1.2.3.pdf
INE-Wireshark-Technologies-1.3.1.pdf
INE-Wireshark-Technologies-1.3.2.pdf
INE-Wireshark-Technologies-1.3.3.pdf
INE-Wireshark-Technologies-2.1.1.pdf
INE-Wireshark-Technologies-2.1.2.pdf
INE-Wireshark-Technologies-2.1.3.pdf
INE-Wireshark-Technologies-2.1.4.pdf
INE-Wireshark-Technologies-2.2.1.pdf
INE-Wireshark-Technologies-2.2.2.pdf
INE-Wireshark-Technologies-2.2.3.pdf
INE-Wireshark-Technologies-2.3.1.pdf
INE-Wireshark-Technologies-2.3.2.pdf
INE-Wireshark-Technologies-2.3.3.pdf
INE-Wireshark-Technologies-2.3.4.pdf
INE-Wireshark-Technologies-2.4.1.pdf
INE-Wireshark-Technologies-2.4.2.pdf
INE-Wireshark-Technologies-2.4.3.pdf
INE-Wireshark-Technologies-2.4.4.pdf
INE-Wireshark-Technologies-2.5.1.pdf
INE-Wireshark-Technologies-2.5.2.pdf
INE-Wireshark-Technologies-2.5.3.pdf
INE-Wireshark-Technologies-2.6.1.pdf
INE-Wireshark-Technologies-2.6.2.pdf
INE-Wireshark-Technologies-3.1.1.pdf
INE-Wireshark-Technologies-3.1.2.pdf
INE-Wireshark-Technologies-3.1.3.pdf
INE-Wireshark-Technologies-3.2.1.pdf
INE-Wireshark-Technologies-3.2.2.pdf
INE-Wireshark-Technologies-3.3.1.pdf
INE-Wireshark-Technologies-3.3.2.pdf
INE-Wireshark-Technologies-3.4.1.pdf
INE-Wireshark-Technologies-3.4.2.pdf
INE-Wireshark-Technologies-3.5.1.pdf
INE-Wireshark-Technologies-3.5.2.pdf
INE-Wireshark-Technologies-3.6.1.pdf
INE-Wireshark-Technologies-3.6.2.pdf
INE-Wireshark-Technologies-3.7.1.pdf
INE-Wireshark-Technologies-3.7.2.pdf
INE-Wireshark-Technologies-3.8.1.pdf
INE-Wireshark-Technologies-3.8.2.pdf
INE-Wireshark-Technologies-3.9.1.pdf
INE-Wireshark-Technologies-3.9.2.pdf
INE-Wireshark-Technologies-4.1.1.pdf
INE-Wireshark-Technologies-4.2.1.pdf
INE-Wireshark-Technologies-4.2.2.pdf
INE-Wireshark-Technologies-4.2.3.pdf
INE-Wireshark-Technologies-4.3.1.pdf
INE-Wireshark-Technologies-4.3.2.pdf
INE-Wireshark-Technologies-4.3.3.pdf