در حال حاضر محصولی در سبد خرید شما وجود ندارد.
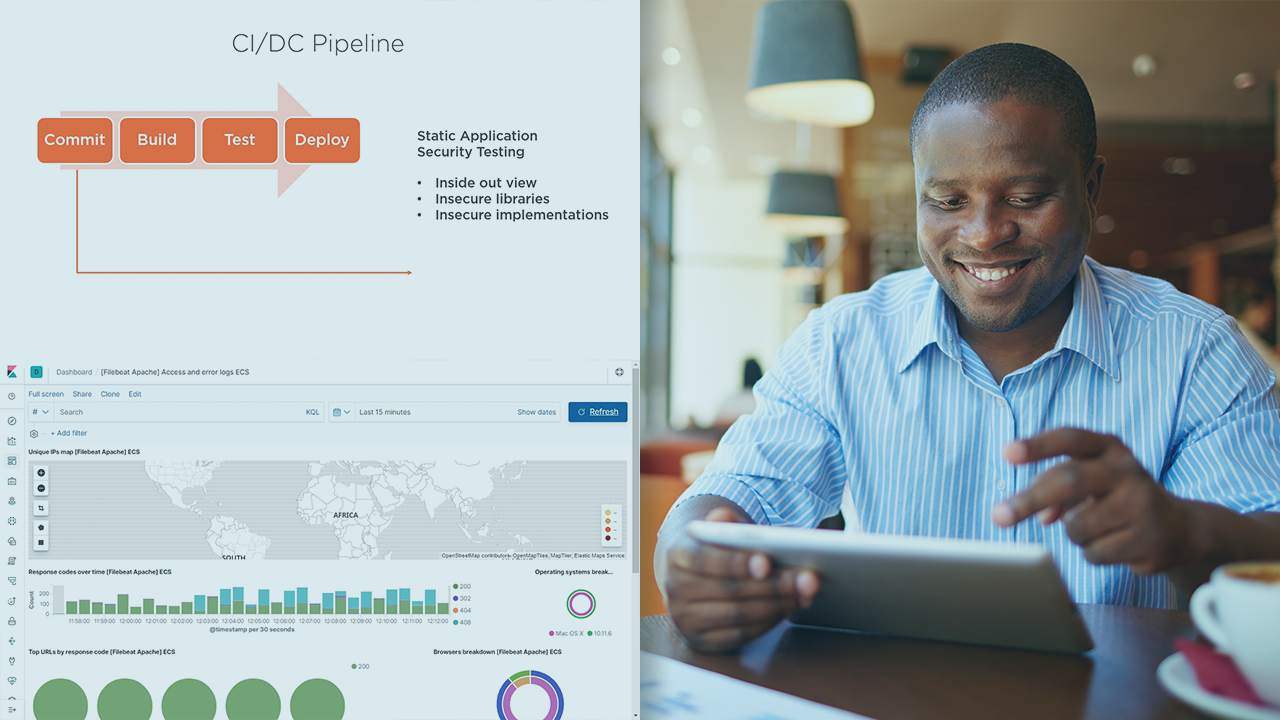
In this course on revealing web application attack methodology, you will explore the use of web application filters, app service logs, and web vulnerability scanners to reveal various advanced attacker techniques and detecting live web exploitations.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


فیلم یادگیری ضد هک Command and Control with Covenant

آموزش آنالیز سیستم عامل بوسیله HELK

فیلم یادگیری Security Event Triage: Revealing Attacker Methodology in Web Application Events

OS Analysis with HELK

آموزش انجام آنالیزهای امنیت در شبکه

Security Event Triage: Operationalizing Security Analysis

Trickbot Banking Trojan

پاسخ به حادثه: تشخیص و تجزیه و تحلیل

Security Event Triage: Detecting Network Anomalies with Behavioral Analysis

Threat Hunting: Hypothesize and Plan
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها