در حال حاضر محصولی در سبد خرید شما وجود ندارد.
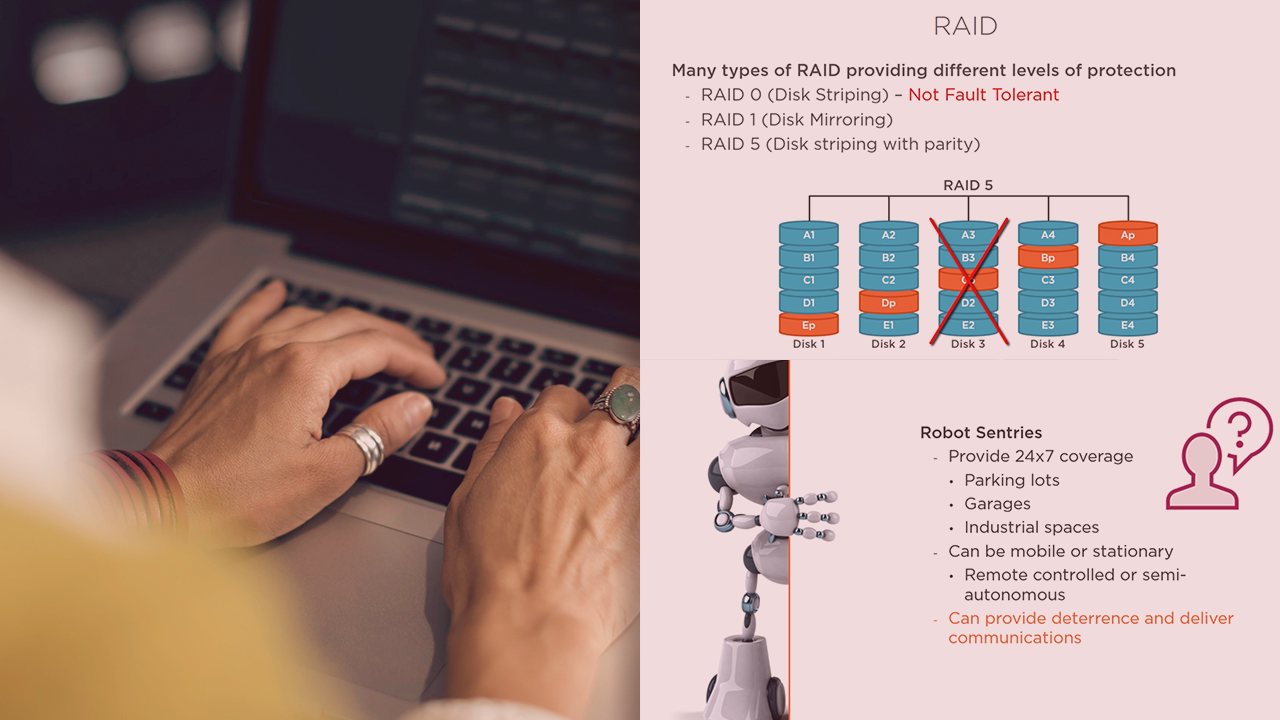
This course will teach you the fundamentals and key concepts around the security architecture and design, and how your organization implements and utilizes various tools and technologies to secure the environment.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


Implementation of Secure Solutions for CompTIA Security+

Cryptography and PKI for CompTIA Security+

Attacks, Threats, and Vulnerabilities for CompTIA Security+

CompTIA Security+: Exam Briefing

Technologies and Tools for CompTIA Security+

Cybersecurity and Artificial Intelligence

آموزش Threat Intelligence

Architecture and Design for CompTIA Security+

Identity and Access Management for CompTIA Security+

Attacks, Threats, and Vulnerabilities for CompTIA Security+
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها