1. Course Overview
2. What is the SSCP Toolbox
3. Who are you
4. What does your study plan look like
5. What is your timeline
6. Comply with Codes of Ethics
7. Understand Security Concepts
8. Identify & Implement Security Controls
9. Functional Security Controls
10. The Asset Management Lifecycle - First Half
11. The Asset Management Lifecycle - Second Half
12. The Change Management Lifecycle
13. Implementing Security Awareness & Training
14. Collaborate with Physical Security Operations
15. Security Operations & Administration - Key Points
16. SingleMulti-factor Authentication (MFA)
17. Single Sign-On (SSO)
18. Spotlight on Kerberos
19. Device Authentication
20. Federated Access
21. Support Internetwork Trust Architectures
22. The Identity Management Lifecycle
23. Understand and Apply Access Controls
24. Understand Security Models
25. Access Controls - Key Points
26. Risk Management Concepts - Vocabulary
27. Spotlight on Business Impact Analysis (BIA)
28. Risk Management Concepts - Impact Assessments
29. Risk Management Concepts - Threat Modeling
30. Risk Management Concepts - Threat Intelligence
31. Risk Tolerance & Treatment
32. Risk Management Frameworks
33. Spotlight on the Risk Management Framework (RMF)
34. Risk Visibility & Reporting
35. Legal & Regulatory Concerns
36. Spotlight on the GDPR
37. Security Assessment & Vulnerability Management
38. Spotlight on Risk Review
39. Operate & Monitor Security Platforms
40. Analyze Monitoring Results
41. Risk Identification, Monitoring & Analysis - Key Points
42. Support the Incident Lifecycle
43. Forensic Investigations - Legal
44. Forensic Investigations - Evidence Handling
45. BCP & DRP - Planning
46. BCP & DRP - Backup & Redundancy
47. BCP & DRP - Alternate Strategies
48. BCP & DRP - Testing & Drills
49. Incident Response & Recovery - Key Points
50. Reasons & Requirements for Cryptography
51. Cryptography Concepts - Hashing & Salting
52. Cryptography Concepts - Encryption
53. Cryptography Concepts - Non-repudiation
54. Spotlight on Secure Protocols
55. Spotlight on IPsec
56. Public Key Infrastructure (PKI) Systems
57. Cryptography Concepts - Cryptographic Attacks
58. Cryptography - Key Points
59. Spotlight on the OSI Model
60. Spotlight on Internet Protocol (IP) networking
61. Topologies, Relationships & Transmission Types
62. Software-Defined Networking (SDN)
63. Network Attacks
64. Manage Network Access Controls
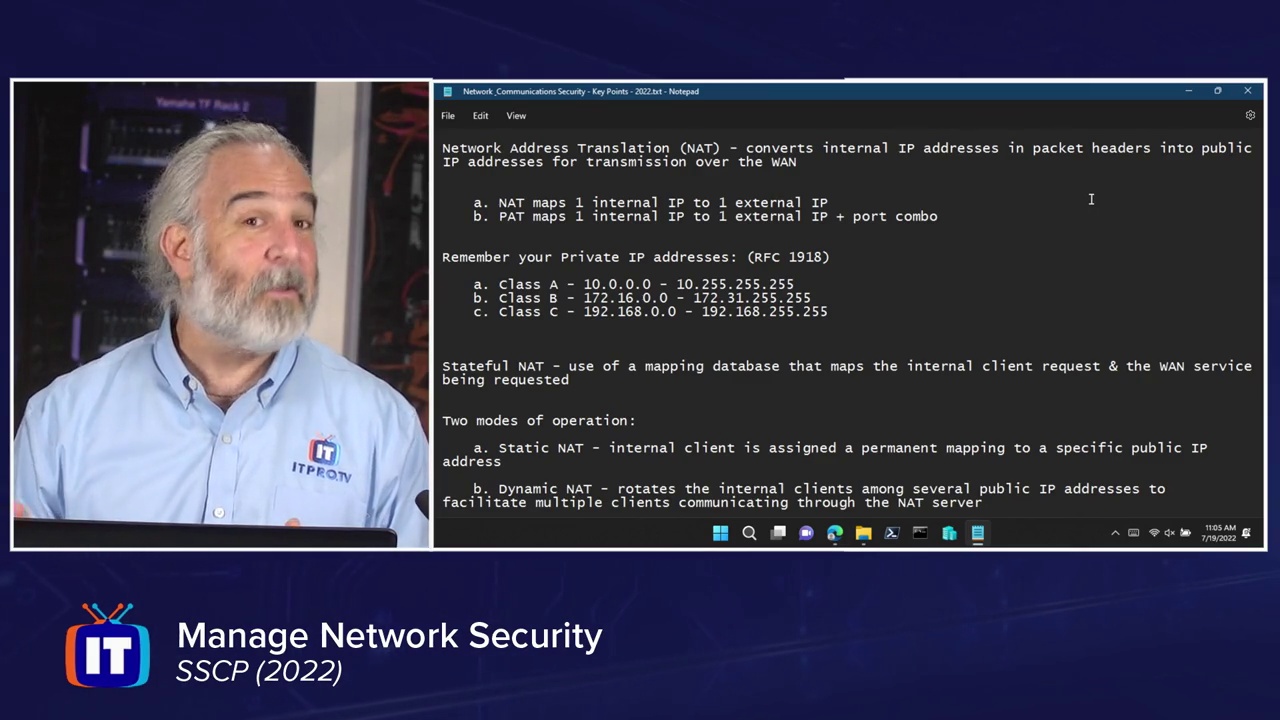
65. Manage Network Security
66. Network-based Security Devices
67. Secure Wireless Communications
68. Network & Communications Security - Key Points
69. Malicious Code & Activity
70. Implement & Operate Endpoint Device Security
71. Administer Mobile Device Management (MDM)
72. Cloud Security - Basics
73. Cloud Security - Legal & Regulatory Concerns
74. Cloud Security - Data
75. Cloud Security - Third party & outsourcing
76. Secure Virtual Environments
77. Systems and Application Security - Key Points