در حال حاضر محصولی در سبد خرید شما وجود ندارد.
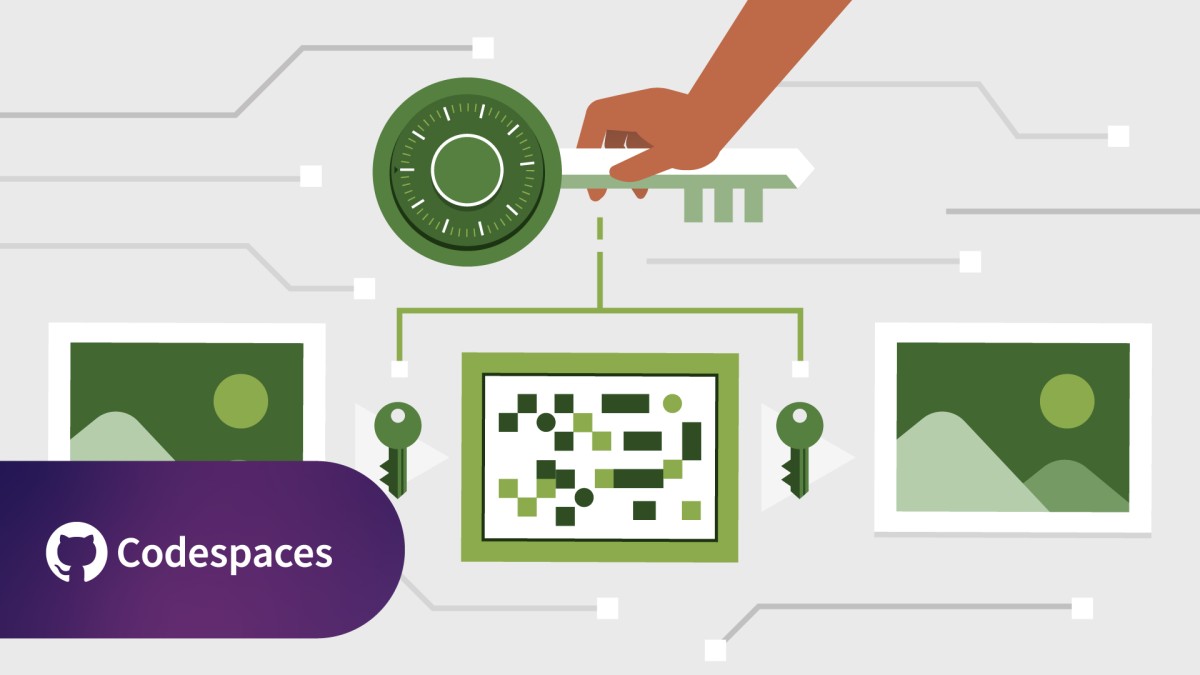
If you work with computers, you use cryptography. Symmetric cryptography is a common method that uses the same key for encryption and decryption of data. Faster and less resource-intensive than asymmetric cryptography, symmetric cryptography is important for all IT professionals to understand. This course delivers a practical overview of the technology, emphasizing high-level concepts that affect how our data is stored and transmitted. Jeremy Hansen explains the difference between single key (symmetric) and multiple key (asymmetric) algorithms, and shows how symmetric encryption affects underlying binary data. Learn about the basic ciphers used in symmetric cryptography, including substitution, permutation, and transposition, and influential symmetric-key algorithms like the Advanced Encryption Standard and its predecessor, the Data Encryption Standard. Review modern block cipher modes like cipher block chaining (CBC), cipher feedback (CFB), and counter (CTR), which can help secure large amounts of data.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.

✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها