در حال حاضر محصولی در سبد خرید شما وجود ندارد.
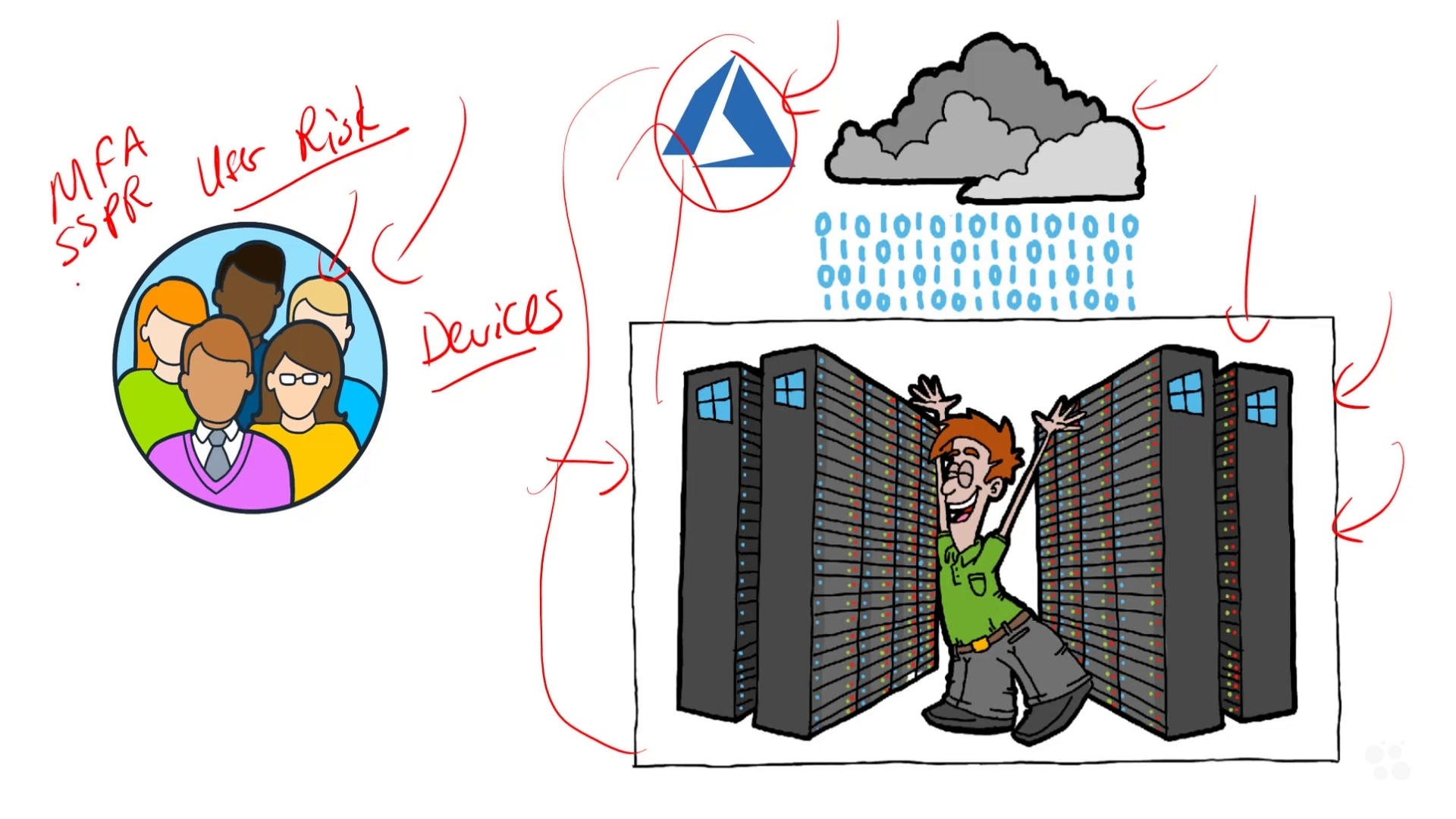
This intermediate Microsoft Security Administrator Associate training prepares security professionals to take the MS-500 exam, which is the one required exam to earn the Microsoft 365 Certified: Security Administrator Associate certification.
Plenty of professions and industries depend on certifications to measure the abilities and competence of the people who work in the field. But few industries have as many different technologies, providers and authorities as the IT field. Within IT as a whole, systems administration in particular has many different certifications. A sysadmin who wants to advance in their career needs to demonstrate technological competence in different softwares, hardwares, concepts and capabilities. With this training, you’ll be prepared to certify as a security administrator associate for Microsoft 365, a certification that can prepare you for future roles in security or systems administration.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.
-main-resized.jpg)
کورس مهندسی کلود Google

Enterprise Administrator Expert (MS-101) Online Training

Security Administrator Associate Online Training

Messaging Administrator Associate Online Training

Microsoft Certified: Power Platform Fundamentals (PL-900) Online Training

آموزش گواهینامه SC-900 Microsoft امنیت ، انطباق و اصول هویت
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها