در حال حاضر محصولی در سبد خرید شما وجود ندارد.

Computer forensics is used to find legal evidence in computers, mobile devices, or data storage units. This course covers all the technical essentials for up-and-coming digital forensics professionals. Instructor Jungwoo Ryoo reviews the goals of computer forensics, the types of investigations it's used for, a forensic investigator's typical tool set, and the legal implications of this type of work.
Explore different specializations currently available in the field to assess your career prospects as an investigator. Jungwoo shows you how to prepare for an investigation, acquire data, ensure data is kept in its original state with software and hardware write-blockers, analyze the data, and generate a report of your findings. Along the way, you’ll discover options for both open-source and commercial software to help find the best tool for your needs and your budget.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.

-main-resized.jpg)
پایتون: الگوهای طراحی
-Cert-Prep--Domains-57-main-resized.jpg)
فیلم یادگیری Certified Analytics Professional (CAP) Cert Prep: Domains 5-7
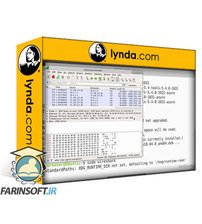
آموزش حفاظت از شبکه تان بوسیله نرم افزارهای Open Source

دوره یادگیری جرم شناسی رایانه ای – Learning Computer Forensics

الگوهای طراحی در زبان Python

Cert Prep: Certified Analytics Professional (CAP)
-Cert-Prep--Domains-14-main-resized.jpg)
فیلم یادگیری Certified Analytics Professional (CAP) Cert Prep: Domains 14

آموزش توسعه نرم افزارهای امن

فیلم یادگیری جرم شناسی دیجیتال از سیستم های عامل Operating system forensics

آشنایی با شغل ها و گواهینامه های Data Science و تحلیل داده ها