1.1 1.Contrast & Compare Information Security Roles - CompTIA Security+ Attacks, Threats and Vulnerabilities.pdf
1. Compare and Contrast Information Security Roles
2.1 2.Compare and Contrast Security Controls and Framework Types.pdf
2.2 How To Use (And Not Use) The NIST CSF.html
2. Compare and Contrast Security Controls and Framework Types
3.1 3.Types of Threat Actors and Attack Vectors.pdf
3. Types of Threat Actors and Attack Vectors
4.1 4.Threat Intelligence & Threat research Sources.pdf
4. Threat Intelligence & Threat Research
5.1 5. Commands used in Assessing Network layout & Security.pdf
5. Commands used in Assessing Network layout & Security
6.1 6. Security concerns regarding Vulnerabilities.pdf
6. Security concerns regarding Vulnerabilities
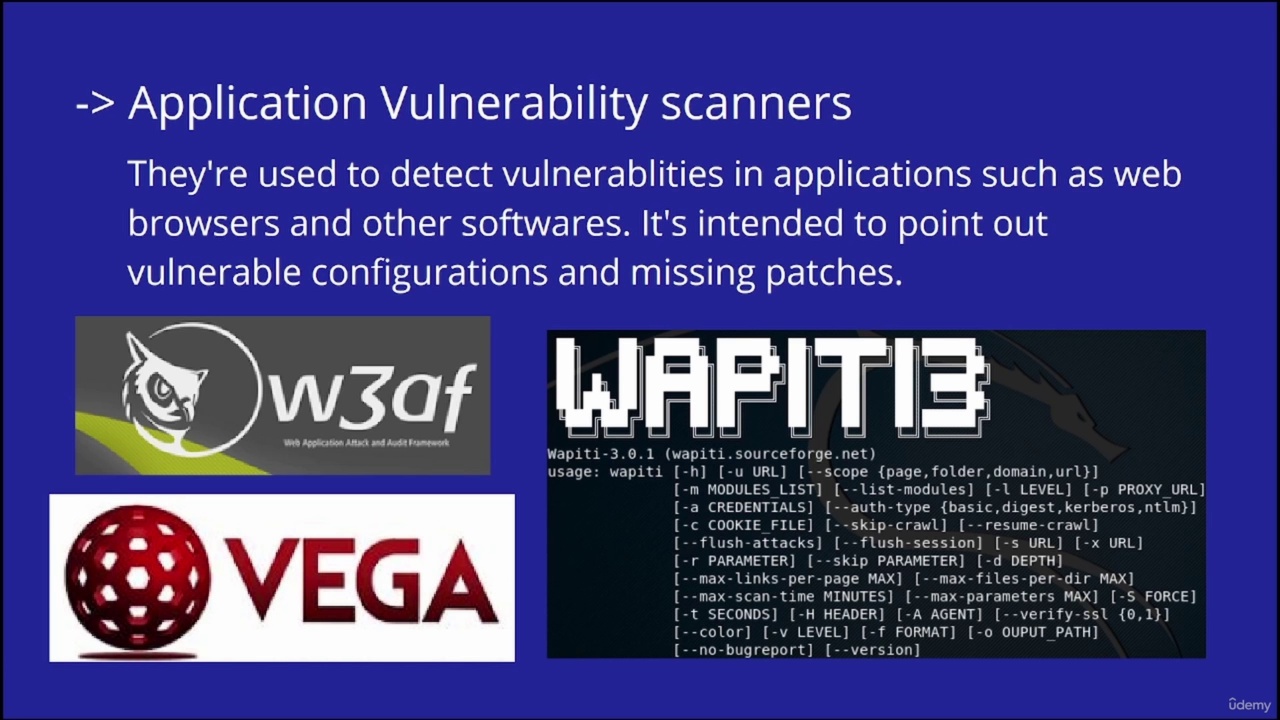
7.1 7.Vulnerability Scanning Techniques and Vulnerability scores & exposures.pdf
7. Vulnerability Scanning Techniques and Vulnerability scores & exposures
8.1 9.Social Engineering Attacks & Principles.pdf
8. Social Engineering Attacks & Principles
9.1 10.Malware and Types of malwares.pdf
9. Malware and Types of malwares