در حال حاضر محصولی در سبد خرید شما وجود ندارد.

Understanding—and successfully implementing—security concepts is essential to using AWS as your enterprise solution. In this course, instructor Sharif Nijim couples pragmatic advice with practical examples that educate IT pros on how to create a secure infrastructure within Amazon Web Services. Explore the shared responsibility model of security, which splits duties between your company and AWS. Deep dive into key identity and access management concepts, including users, groups, roles, and policies. Find out how to create a secure infrastructure within AWS. Plus, complete several hands-on challenges that enable you to work independently and develop solutions on topics including IAM roles, KMS, S3, and data breaches.
در این روش نیاز به افزودن محصول به سبد خرید و تکمیل اطلاعات نیست و شما پس از وارد کردن ایمیل خود و طی کردن مراحل پرداخت لینک های دریافت محصولات را در ایمیل خود دریافت خواهید کرد.


آموزش کامل Amazon Lightsail

آموزش پیاده سازی High Availability در کلود AWS
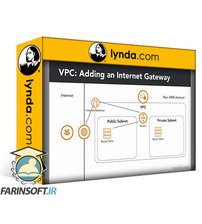
آموزش شبکه سازی در Amazon Web Services

آموزش کامل Enterprise Security در کلود AWS

AWS: امنیت و انطباق
-main-resized.jpg)
نکات آزمون: AWS Certified Sysops Administrator (SOA-C02)

آموزش پیاده سازی High Availability در کلود AWS

دوره یادگیری نکات لازم برای آزمون بین المللی AWS Certified SysOps Administrator

کورس کامل Enterprise Security در کلود AWS

آموزش شبکه سازی در کلود AWS
✨ تا ۷۰% تخفیف با شارژ کیف پول 🎁
مشاهده پلن ها