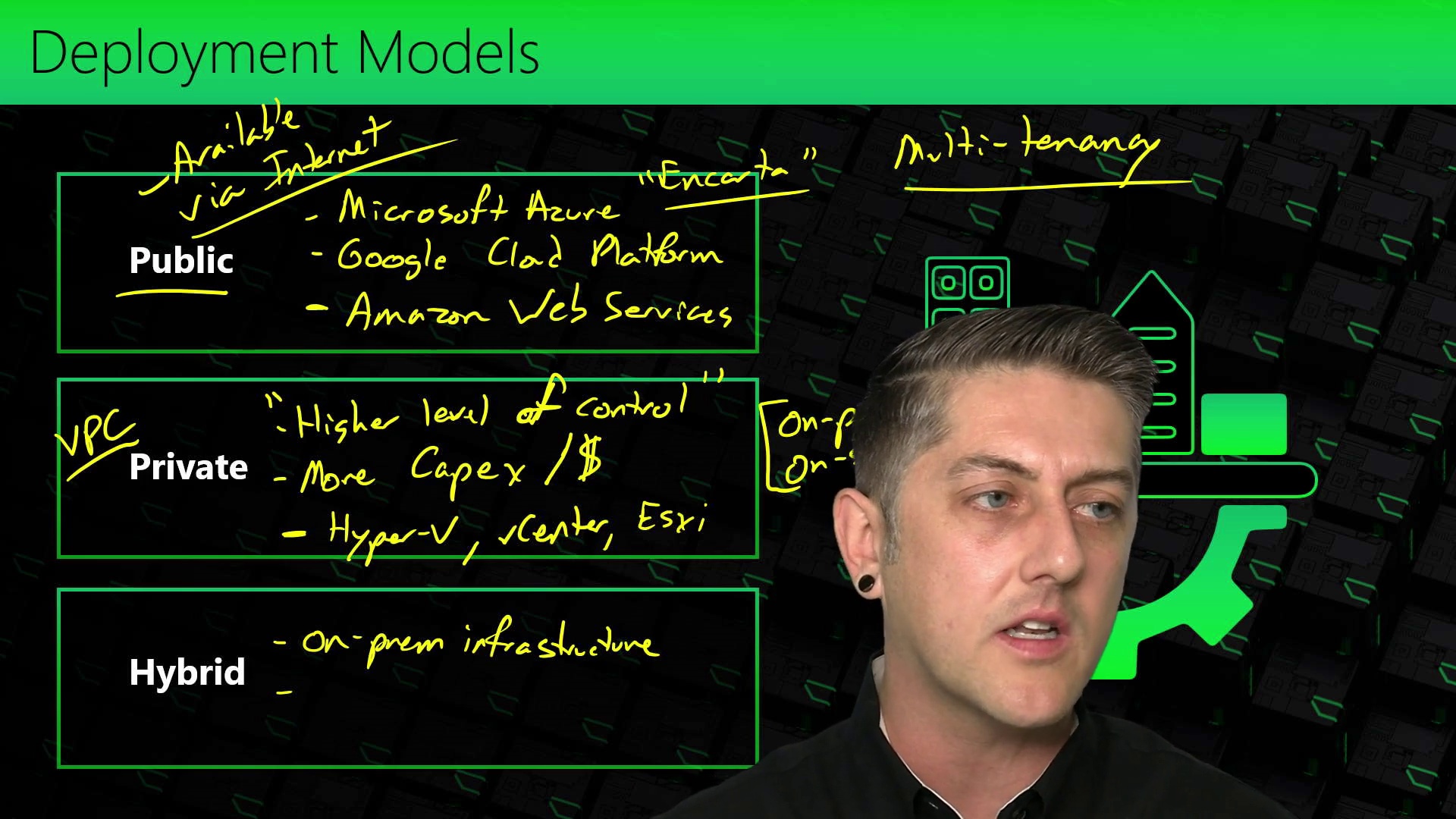
1.Backup Objects
2.Restoration Methods
4.Backup and Restore Policies Cont.
5.Disaster Recovery Tasks (Scenario)
6.Replication
7.Disaster Recovery Requirements
8.Disaster Recovery Documenation
9.Troubleshooting Methodology (Scenario)
10.Troubleshooting Methodology
11.Troubleshoot Security Issues (Scenario)
12.Troubleshoot Privilege Issues
13.Troubleshoot Authentication Issues
14.Troubleshoot Authorization Issues
15.Troubleshoot Security Group Issues
16.Troubleshoot Key and Cert Issues
17.Troubleshoot Misconfigured Policy Issues
18.Troubleshoot Data Security Issues
19.Troubleshoot Exposed Endpoint Issues
20.Troubleshoot Misconfigured Security Policies
21.Manage Unsupported Protocols
22.Manage Internal and External Attacks
23.Troubleshoot Deployment Issues (Scenario)
24.Troubleshoot Connectivity Issues
25.Troubleshoot Performance Degradation Issues
26.Troubleshoot Insufficient Capactiy Issues
27.Troubleshoot Vendor Related Issues
28.Troubleshoot Connectivity Issues (Scenario)
29.Troubleshoot Network Security Group Issues
30.Troubleshoot Network Config Issues
31.Troubleshoot Network Config Issues Cont. 1
32.Troubleshoot Network Configu Issues Cont. 2
33.Network Troubleshooting Tools
34.Troubleshoot Performance Issues (Scenario)
35.Troubleshoot Resource Utilization Issues
36.Troubleshoot Resource Utilization Issues Cont. 1
37.Troubleshoot Resource Utilization Issues Cont. 2
38.Troubleshoot Resource Utilization Issues Cont. 3
39.Troubleshoot Application Issues
40.Troubleshoot Load Balancer Failures
41.Troubleshoot Automation and Orchestration (Scenario)
42.Troubleshoot Account Mismatch Issues
43.Troubleshoot Change Management Failure
44.Troubleshoot Identity Change Issues
45.Troubleshoot Automation Tools
46.Troubleshoot Job Validation Issues
47.Troubleshoot Patching Failures