1.1 Introducing the CCNP and CCIE Security Certifications
1.2 Comparing the CCNP and CCIE Security Certifications with Other Cisco Certifications
1.3 Exam Prep Tips
2.1 Cybersecurity Concepts, The NIST Cybersecurity Framework, and Additional NIST Guidance and Documents
2.2 Defining Threats, Vulnerabilities, and Exploits
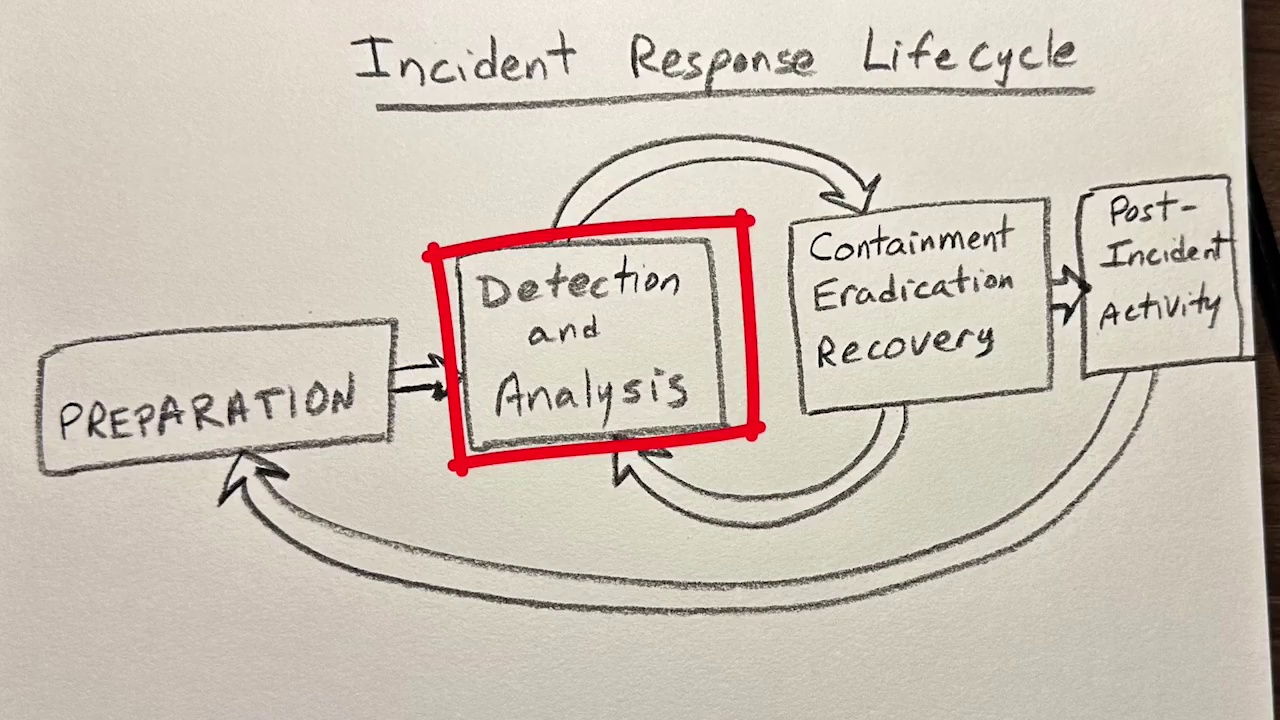
2.3 An Introduction to Incident Response Part 1
2.4 An Introduction to Incident Response Part 2
2.5 ISOIEC 270022022 and NIST Incident Response Guidance
2.6 Understanding Threat Intelligence
2.7 Understanding Threat Hunting
2.8 Common Software and Hardware Vulnerabilities
2.9 Authentication-based Vulnerabilities and the OWASP Top 10
2.10 Malware Types, Payloads, and Transmission Methods
2.11 Malware Communication Methods, and Infection Mechanisms
2.12 Ransomware, Keyloggers, Spyware, and Tips for Analyzing Malware
2.13 Static Analysis s. Dynamic Analysis
3.1 Traditional Networking Planes and Introduction to Software-Defined Networking
3.2 VXLAN and Network Oerlays
3.3 Micro-Segmentation
3.4 Open-Source Initiaties
3.5 Modern Network Architectures and the Cisco Catalyst Center
3.6 Introduction to the Cisco ACI Solution
3.7 Introduction to Network Programmability, Modern Programming Languages, and Tools
3.8 DeNet Resources and Getting Started with APIs
3.9 YANG Models, NETCONF, and RESTCONF
3.10 OpenConfig and gNMI
4.1 Cloud Serice Models and Security
4.2 DeOps, CICD and DeSecOps
4.3 Container Orchestration and Kubernetes
4.4 Sererless Computing
4.5 Introducing DeSecOps
4.6 Patch Management in the Cloud
4.7 Security Assessment in the Cloud, and Questions to Ask Your Cloud Serice Proider
4.8 The Cisco Umbrella Architecture
4.9 Cisco Secure Email Cloud
4.10 Cisco Secure Cloud Analytics
4.11 AppDynamics, Cloud Monitoring, and Cisco Secure Workload
5.1 Content Security Fundamentals
5.2 Cisco Async Operating System (AsyncOS)
5.3 Cisco Secure Web Appliance
5.4 Explicit Forward Mode s. Transparent Mode
5.5 Traffic Redirection with Policy-based Routing
5.6 Cisco Secure Email Threat Defense
5.7 SMTP Authentication and Encryption and DKIM
6.1 Endpoint Threat Detection and Response
6.2 Cisco Secure Endpoint
6.3 Cisco Secure Client
6.4 Cisco XDR
7.1 Introduction to Authentication, Authorization, and Accounting
7.2 Multifactor Authentication and Duo Security
7.3 Understanding the Zero Trust Architecture
7.4 Access Control DAC
7.5 Access Control MAC
7.6 Access Control RBAC
7.7 Access Control ABAC
7.8 AAA Protocols RADIUS, TACACS+, Diameter
7.9 Understanding 802.1X and TrustSec Software-defined Segmentation
7.10 Change of Authorization (CoA)
8.1 Cisco Secure Firewalls and Cisco Next-Generation Intrusion Preention Systems
8.2 Network Access Control List and Firewalling
8.3 VLAN ACLs, Security Group Based ACLs, Downloadable ACLs
8.4 Cisco Identity Serices Engine (ISE)
8.5 Cisco Platform Exchange Grid (pxGrid)
8.6 Cisco ISE Context and Identity Serices; Profiling Serices; and Authorization Rules
9.1 Final Tips for Exam Day
9.2 Where to go now
CCNP and CCIE Security Core SCOR 350-701 (Exam Blueprint 1.1) Introduction
CCNP and CCIE Security Core SCOR 350-701 (Exam Blueprint 1.1) Introduction (1)
CCNP and CCIE Security Core SCOR 350-701 (Exam Blueprint 1.1) Summary
Learning objecties
Learning objecties (1)
Learning objecties (2)
Learning objecties (3)
Learning objecties (4)
Learning objecties (5)
Learning objecties (6)
Learning objecties (7)
Learning objecties (8)