001. Part 1. Foundations
002. Chapter 1. Podman A next-generation container engine
003. Chapter 1. A brief overview of containers
004. Chapter 1. Why use Podman when you have Docker
005. Chapter 1. When not to use Podman
006. Chapter 1. Sumarry
007. Chapter 2. Command line
008. Chapter 2. Working with container images
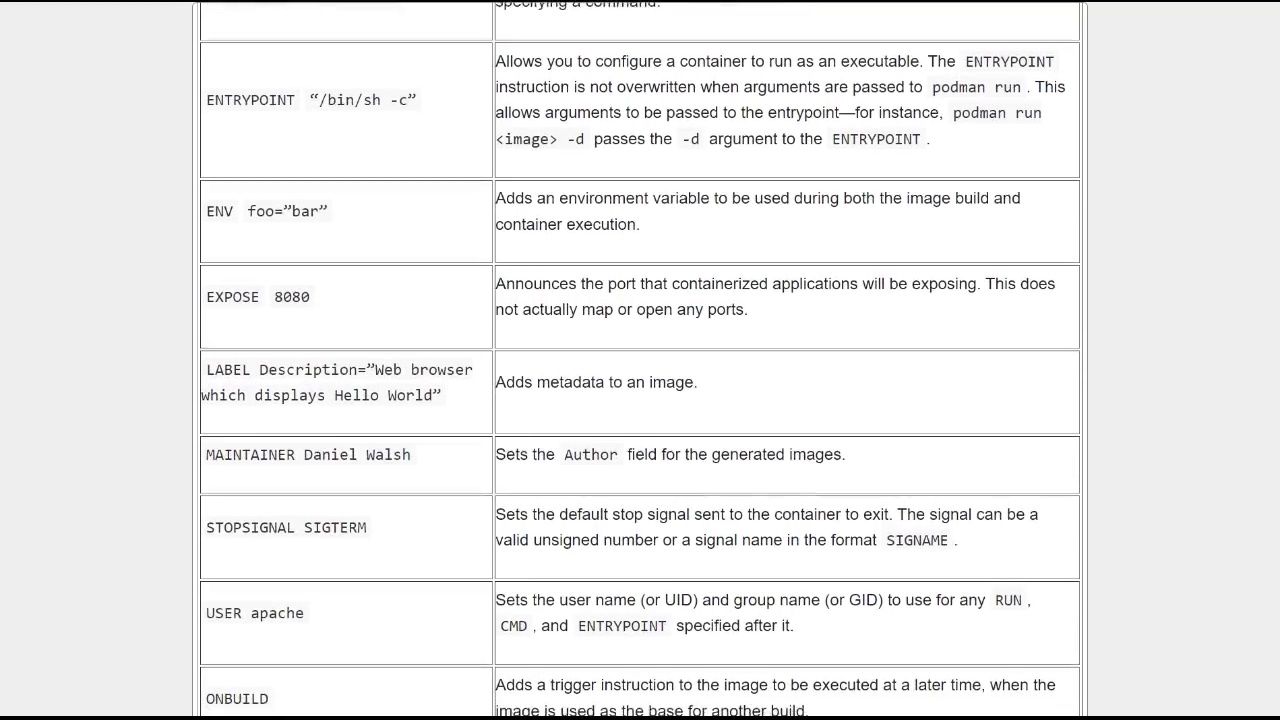
009. Chapter 2. Building images
010. Chapter 2. Summary
011. Chapter 3. Volumes
012. Chapter 3. Summary
013. Chapter 4. Pods
014. Chapter 4. Creating a pod
015. Chapter 4. Adding a container to a pod
016. Chapter 4. Starting a pod
017. Chapter 4. Stopping a pod
018. Chapter 4. Listing pods
019. Chapter 4. Removing pods
020. Chapter 4. Summary
021. Part 2. Design
022. Chapter 5. Customization and configuration files
023. Chapter 5. Configuration files for registries
024. Chapter 5. Configuration files for engines
025. Chapter 5. System configuration files
026. Chapter 5. Summary
027. Chapter 6. Rootless containers
028. Chapter 6. Rootless Podman under the covers
029. Chapter 6. Summary
030. Part 3. Advanced topics
031. Chapter 7. Integration with systemd
032. Chapter 7. Journald for logging and events
033. Chapter 7. Starting containers at boot
034. Chapter 7. Running containers in notify unit files
035. Chapter 7. Rolling back failed containers after update
036. Chapter 7. Socket-activated Podman containers
037. Chapter 7. Summary
038. Chapter 8. Working with Kubernetes
039. Chapter 8. Generating Kubernetes YAML files with Podman
040. Chapter 8. Generating Podman pods and containers from Kubernetes YAML
041. Chapter 8. Running Podman within a container
042. Chapter 8. Summary
043. Chapter 9. Podman as a service
044. Chapter 9. Podman-supported APIs
045. Chapter 9. Python libraries for interacting with Podman
046. Chapter 9. Using docker-compose with the Podman service
047. Chapter 9. podman - -remote
048. Chapter 9. Summary
049. Part 4. Container security
050. Chapter 10. Security container isolation
051. Chapter 10. Linux capabilities
052. Chapter 10. UID isolation User namespace
053. Chapter 10. Process isolation PID namespace
054. Chapter 10. Network isolation Network namespace
055. Chapter 10. IPC isolation IPC namespace
056. Chapter 10. Filesystem isolation Mount namespace
057. Chapter 10. Filesystem isolation SELinux
058. Chapter 10. System call isolation seccomp
059. Chapter 10. Virtual machine isolation
060. Chapter 11. Additional security considerations
061. Chapter 11. Podman secret handling
062. Chapter 11. Podman image trust
063. Chapter 11. Podman image scanning
064. Chapter 11. Security in depth
065. Chapter 11. Summary
066. Appendix A. Podman-related container tools
067. Appendix A. Buildah
068. Appendix A. CRI-O Container Runtime Interface for OCI containers
069. Appendix B. OCI runtimes
070. Appendix B. crun
071. Appendix B. Kata
072. Appendix B. gVisor
073. Appendix C. Getting Podman
074. Appendix C. Building from source code
075. Appendix C. Podman Desktop
076. Appendix C. Summary
077. Appendix D. Contributing to Podman
078. Appendix D. Podman on github.com
079. Appendix E. Podman on macOS
080. Appendix E. Summary
081. Appendix F. Podman on Windows
082. Appendix F. Using podman machine
083. Appendix F. Summary